Hello guys,
today I will talk about how you can setup a virtual DMZ with a virt. Sophos UTM.
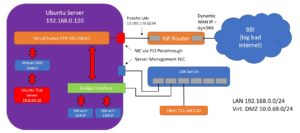
The logical network structure
For a better understanding, I have create a little grafic with the logical network structure.
I am using an Ubuntu server with KVM as hypervisor. My UTM, DMZ and LAN servers only run on the one server.
If you want to know how to set up a virtual UTM, just have a look at my blog entry about it.
https://networkguy.de/sophos-utm-how-to-install-a-virtual-home-firewall-under-ubuntu-via-kvm
Create the virtual switch
First we need a dummy interface.
You can create it with the following commands:
sudo ip link add name "what you want" type dummy sudo ifconfig "what you want" up
For example I have call it “DMZ-Dummy5”
![]()
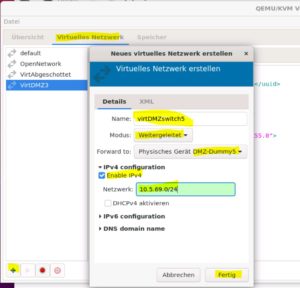
Second create the switch.
Modus = forwarded. You must give it an IP, otherwise there is an error message.
As the last step we have to isolate the server from the virtual DMZ.
For this we need an iptables rule to drop all incoming traffic to the dummy interface. And because it is so beautiful, we also ban outgoing traffic too.
sudo iptables -A INPUT -i Dummy-DMZ5 -j DROP sudo iptables -A OUTPUT -o virbr3 -j DROP sudo iptables-save
For what do we actually need this iptables rule? Quite simple. The DMZ server could access the hypervisor via this interface.
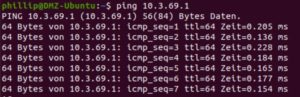
In this example, the hypervisor have in the virtual DMZ network the IP 10.3.69.1/24. The test server have the IP 10.3.69.2/24.
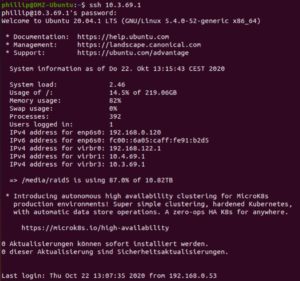
Ping test
ssh access to the hypervisor (not so good for a DMZ)
Connect the DMZ with the UTM and the test server
OK, we have create the virtual DMZ. Now we need a connection with a test server and our virtual UTM.
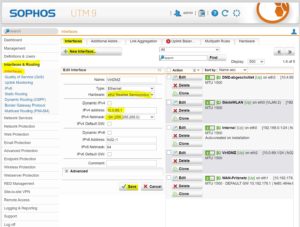
For this example I use the virtual switch VirtDMZ3.
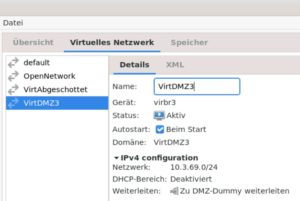
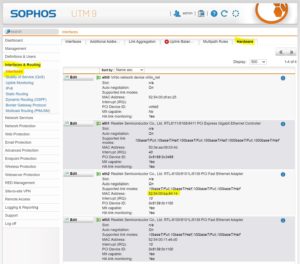
The switch nic is called virbr3, I don’t know why. But you can find it by IP address.
UTM
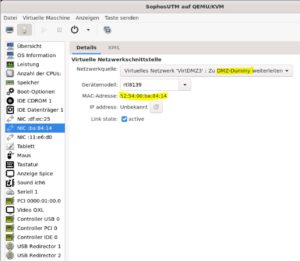
Connect the virtual switch as an additional NIC.
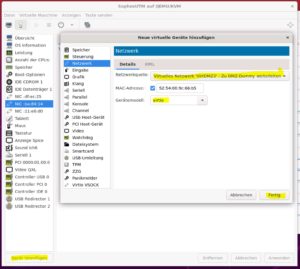
Test server
For the test server, use the virtual switch as NIC.
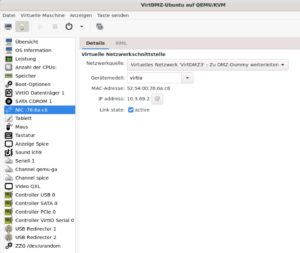
Needed configurations on the UTM
insert the new DMZ interface
You can find the correct interface using the MAC address. Compare it with the Virt Manager and the UTM.
Network Services
DNS
Don’t do this! If you allow the DMZ devices to use the DNS service of the UTM, DNS queries can be made via all devices known to the UTM. Every hacker is happy about this.
negative example:
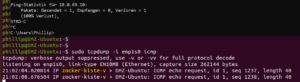
The DMZ device can resolve the IP address from my LAN client.
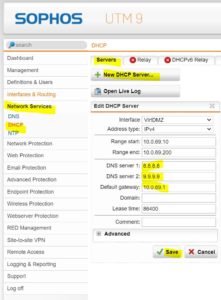
DHCP
If you want a DHCP, use for DNS open DNS server like google DNS or quad9.
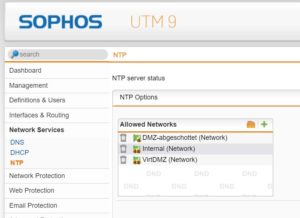
NTP
I recommend, to use the UTM own NTP service for your devices. The fewer external services allowed, the better.
Network Protection
Firewall
For the DMZ you need 2 firewall rules. One for the internet access and one for the management.
The permitted services are only exemplary. Just check which services you need and allow them.
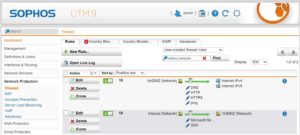
ICMP
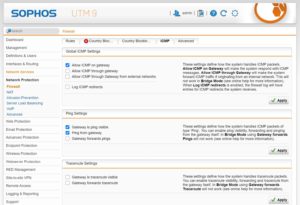
The UTM has the special feature that ping is also handled under ICMP and can overwrite firewall rules if ping is prohibited. Therefore you should disable pinging via the gateway interface and enable firewall rules if required. Otherwise it would be possible that DMZ devices can map the IP network structures via IP scanner.
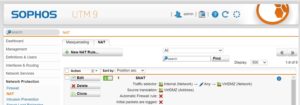
NAT
I recommend to use a SNAT rule for accessing the DMZ, so that no conclusions can be drawn from the communication to the rest of the network.
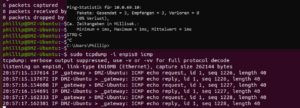
without SNAT rule:
You can see the IP from my client

with SNAT rule:
You see only the UTM DMZ gateway.
That’s all
Have a nice day!










2 Responses
super expression thanks
Hi Murat, thanks for your nice comment.