Hello guys!
I had the task to secure VMware Horizon via the Sophos XG WAF.
In this example we have a VMware Horizon server with the IP 192.168.100.20.
The Sophos XG DMZ interface has the IP 192.168.100.1.
The following steps were necessary:
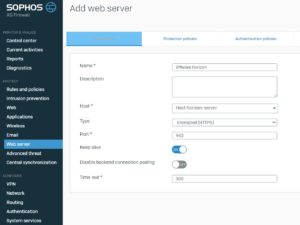
Create a new Webserver definition
For a better searce. I write Host for a client/server or LAN for a network before a definition name. In this example Host horizon-server.
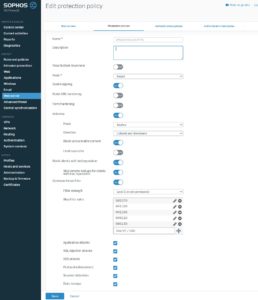
Create the WAF policy
skip filter rules:
920370
941100
941160
949110
980130
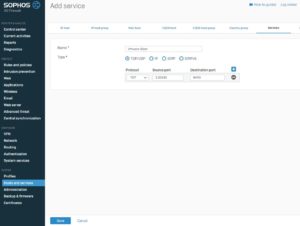
Create the VMware Blast protocol definition
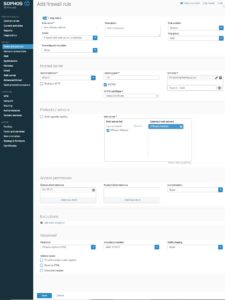
Create the WAF firewall rule
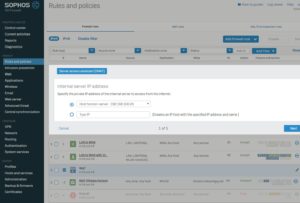
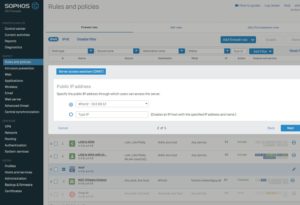
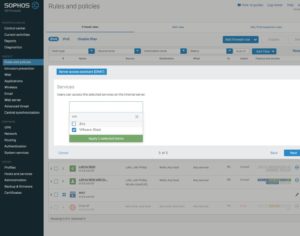
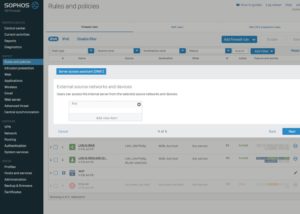
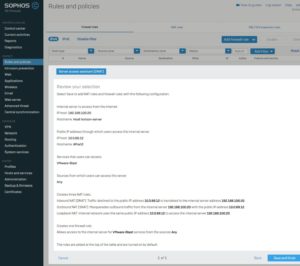
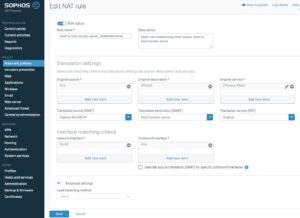
Create a NAT rule for the VMware blast protocol with the Server access assistant
That isn’t a security problem. Before using the blast protocol, the user must be authenticated by the Horizon server which is protected by the WAF.
After Franks hint in the comments. If you need PCoIP for Teradici ZeroClients you have to add port 4672 UDP with a second DNAT Rule.
And now here comes the tricky part.
The Horizon server (192.168.100.20) is protected by the WAF and from its perspective the server is only communicating with the Sophos XG (192.168.100.1).
But as soon we have the protocol change to blast (port 8443) we can’t use the WAF and a classic DNAT dosn’t change the source IP. (In this case a random WAN IP from the Users ISP).
But why do we need this? Because, if the user comes with his original WAN IP, the Horizon server says “I don’t know you. You have not authenticated with me. Get lost” and cuts the connection.
Therefore we must adjust the DNAT rule for the blast protocol.
We must activate a SNAT with the DMZ IP from the Sophos XG (192.168.100.1).
Finaly from the point of view of the Horizon server we now also have no changed communication partner by a protocol change.
Have a nice day!









2 Responses
Hi,
keep in mind, this is only working with vmware Blast. If you still need PCoIP (maybe for Teradici ZeroClients), you have to add port 4672 UDP also.
regards,
Frank
Hello Frank,
thanks for the hint. Only the blast protocol was required in the environment. I’ll include your hint in the article in a moment.
regards,
Phillip