Hello guys,
today I will talk about how you can setup a site to site VPN with 2 Sophos UTM and dynDNS.
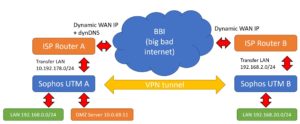
The logical network structure
For a better understanding I have create a little grafic with the logical network structure.
The UTMs stands behind a ISP Router with a private transfer LAN IP and the routers have no static WAN IP.
Only router A is available via dynDNS.
preparatory work on the ISP routers
Before we can create a Site to Site VPN tunnel, we must create a portforwarding roule on ISP Router A. OK, and way do we not need a portforwarding rule for the ISP Router B? Site B have not a dynDNS and because this, UTM A do not known the actual WAN IP from Router B and is not able to initiate a tunnel to UTM B. Only UTM B is able to initiate a VPN tunnel to Site A.
In this example i have a router from AVM which is widely used in Germany. The router has a function named “Exposed Host”. This is a portforwarding rule to send all incoming traffic from all ports to the configured host. Except ports for router’s own services or expected response packets from other clients in the transfer LAN (10.192.178.0/24) which are handled by the router stateful inspection firewall.
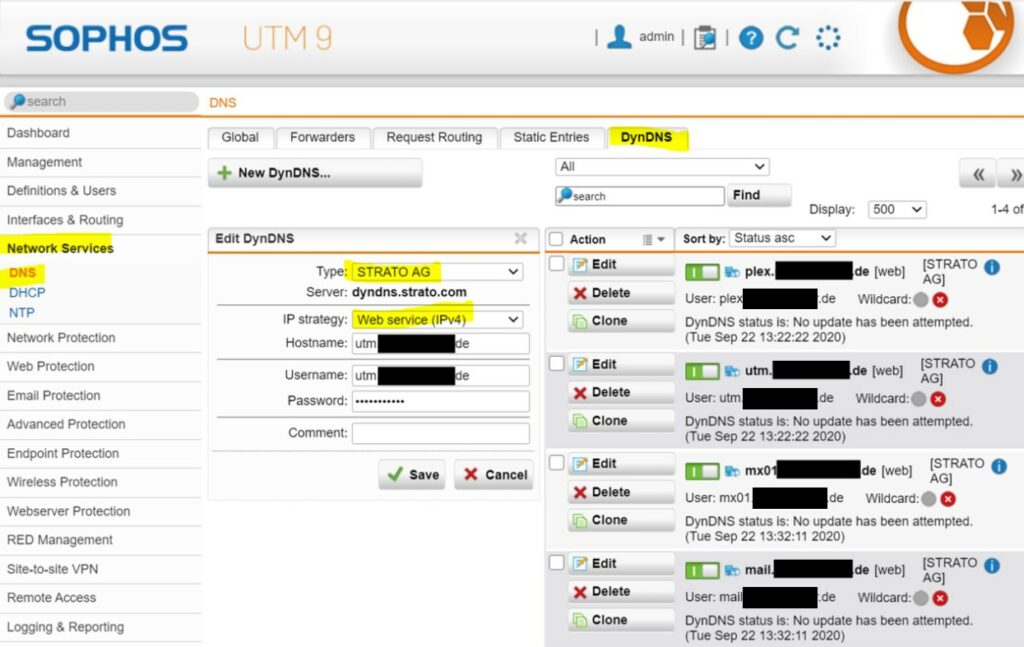
dynDNS
Because we are in the unbelievable situation of not having fixed WAN IP addresses, we have to use dynDNS. You can use a dynDNS service from the ISP Router or from the UTM. In my case I have use the dynDNS service from my UTM and as dynDNS provider the German Strato AG.
build the tunnel
OK, now we can build the VPN tunnel. For a site to site VPN tunnel is IPSec the recommended solution. And please to not use a PSK for authentication. A RSA key or a X509 certificate is the more adult solution. The use of PSKs is out of date.
I use the RSA key.
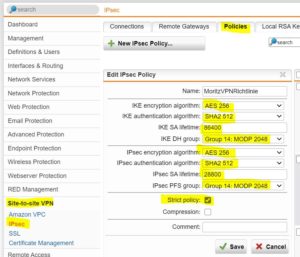
- create a policy
First you must create a policy. The policy must be identical on boot sites. This is a problem I have often encountered in my everyday life:)
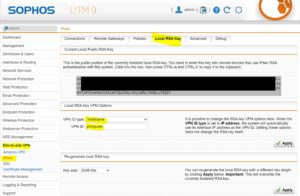
- Edit the local RSA Key
For our VPN tunnel we must edit the RSA Key settings. For VPN ID you must set hostname enter the UTM hostname under VPN ID.
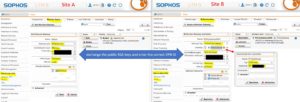
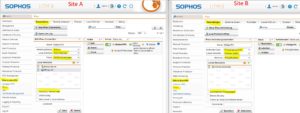
Site A
Site B
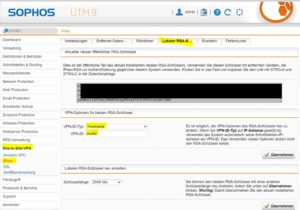
- Remote Gateway Settings
Now we must create the Remote Gateway on both sites. Enter the public RSAkey in the other Sophos UTM and act on the correct VPN ID. Site A will be set to answer only and site B to initiate connection.
- Connections
Now we have to do the last adjustments for the vpn tunnel. I don’t recommend to use the auto firewall rules, because they allow Any and in our example, we also have a DMZ server that should be accessible via VPN. And Any would not be so cool here.
- Turn on the tunnel
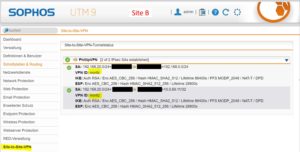
OK, now we can activate the VPN tunnel on both sites and can see it comes up.
Create the firewall rules
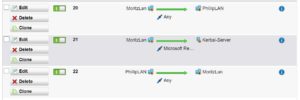
Now the tunnel is online but the firewall rules are still missing.
Example firewall rules Site A
Test the connection
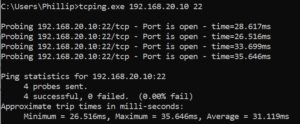
Ping is not a good test. If it is possible test the seperate needed services. ICMP is treated separately in the UTM and can easily lead you on the wrong track. I like to use the tool tcping.exe
Test from my client 192.168.0.53 to a Linux server 192.168.20.10 with port 22 ssh.
Have a nice day!









4 Responses
thanks
thanks, no problem ;)
Hi all, with which router model / brand can I create a site to site VPN between the Sophos UTM Firewall in my work and my home so that I can connect the ethernet phone to my home and that it connects in vpn to the vlan of the pbx at work?
And what ports should I open on my isp router?
Hello, it’s possible with a AVM Fritzbox. Alternatively you could also try it with a softphone. Personally, I would avoid connecting my private LAN to my company network unless it is absolutely necessary.