Phew… it cost me a lot of time and headaches to establish the scenario of 802.1x and mac-authentication with dynamic VLAN assignment on a ProCurve/aruba Switch. The NPS logs set me on the wrong track… I used VLAN 1 for 802.1x, VLAN 2 for MAC-Authentication and VLAN 999 for the dead VLAN. Don’t forget to configure them, otherwhise your dynamic VLAN assignment won’t work! My test scenario:
- Microsoft Windows Server 2016
- Active Directory
- Certificate Authority
- Network Policy Server
- HP ProCurve 2910al-24G (J9145A) with firmware W.15.14.0016
- A Windows Client (joined the AD domain)
- A Printer
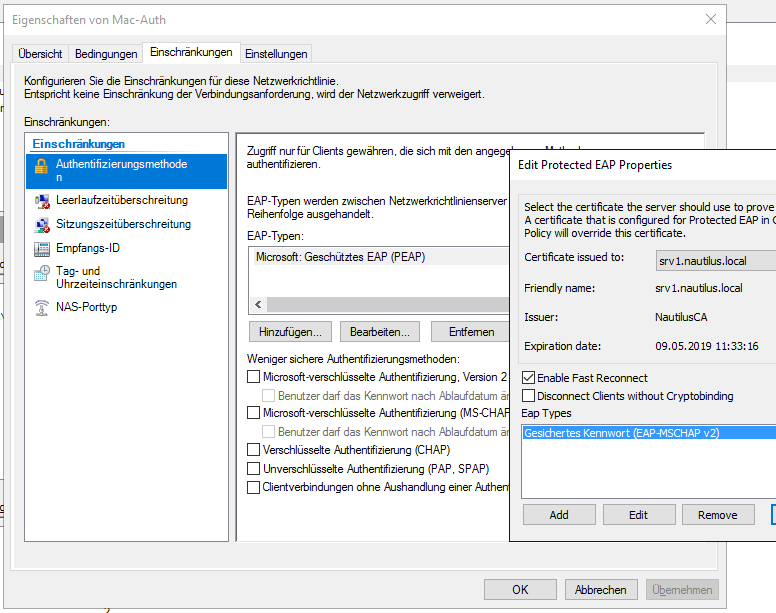
The server was connected to Port 24 (vlan 1 untagged). The other ports were configured in the dead vlan 999. The NPS will be configured as in my older tutorial (https://networkguy.de/?p=1649) except the MAC-Authentication policy. Here we need to configure Protected EAP with MS-CHAPv2:
to configure PEAP for both authentication methods, configure this:
aaa authentication port-access eap-radius aaa authentication mac-based peap-mschapv2
I tested it with the first four ports. You will need to configure this settings to all edge-ports later:
aaa port-access authenticator 1-4 aaa port-access authenticator 1 client-limit 1 aaa port-access authenticator 2 client-limit 1 aaa port-access authenticator 3 client-limit 1 aaa port-access authenticator 4 client-limit 1 aaa port-access authenticator active
mac-authentication parameters:
aaa port-access mac-based 1-4 aaa port-access mac-based 1 addr-limit 1 aaa port-access mac-based 2 addr-limit 1 aaa port-access mac-based 3 addr-limit 1 aaa port-access mac-based 4 addr-limit 1
I didn’t found a working solution on the web so I hope I can help other people with this. Feel free to comment!
Have a nice and sunny day!