Hello guys! Today I want to show you how to secure your edge-switches with 802.1x and mac-authentication fallback in combination with HPE comware-based switches. The 802.1x protocol is used for network access control. For devices like printers, cameras, etc. we will use mac-authentication as a fallback. We will also use dynamic VLAN assignment for the connected ports.
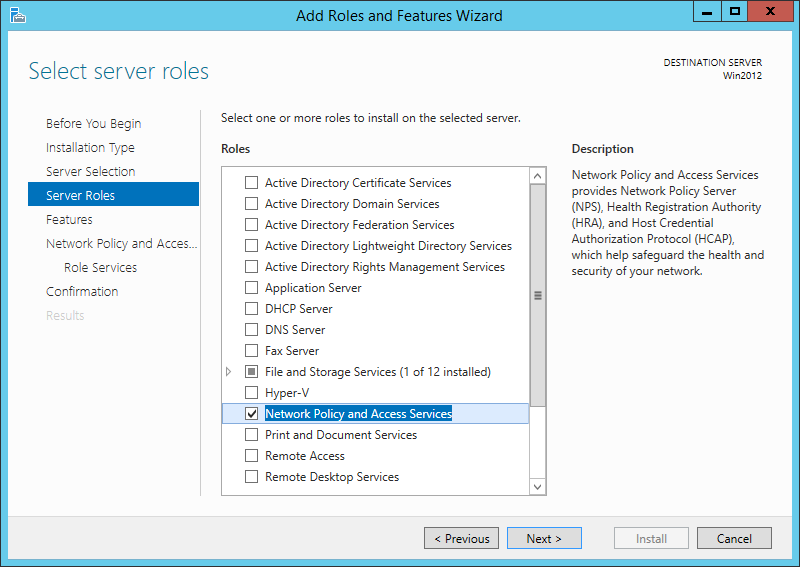
Our radius server will be Microsoft NPS. You can activate this role on the Windows server:
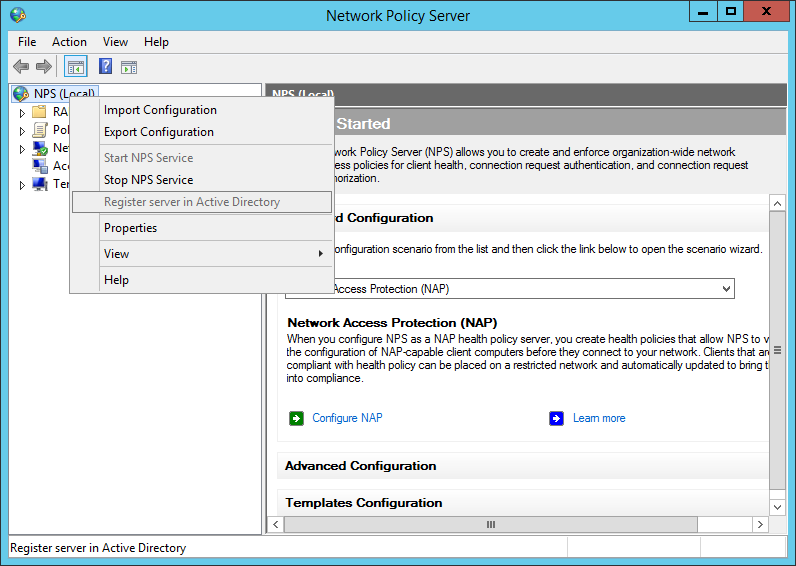
After the installation, open the NPS console and register the radius server in your Active Directory:
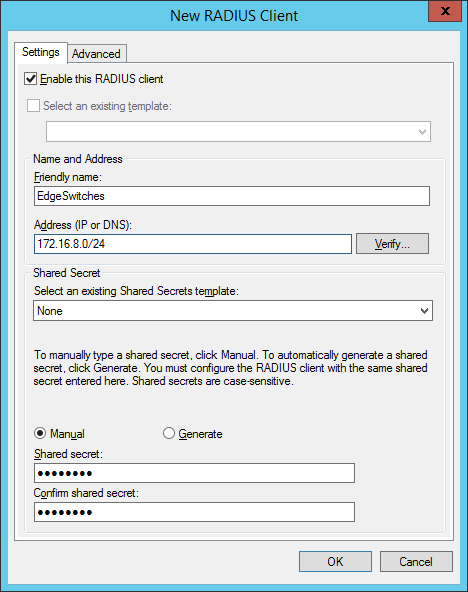
add your switches or your management network as a radius-client:
the shared secret will be used in the switch configuration. In created two groups within my test environment:
- “VLAN2-802.1x” containing computer accounts
- “VLAN3-MAC-Auth” containing user accounts (username+password = mac-address of the device)
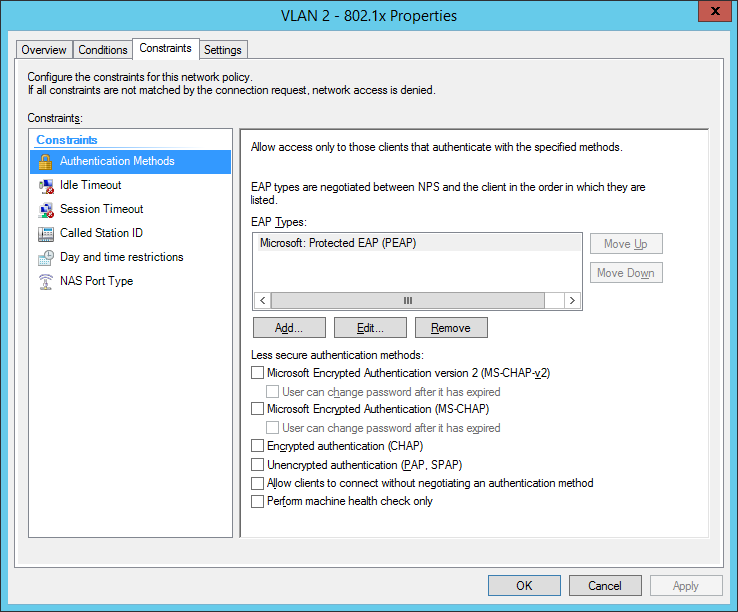
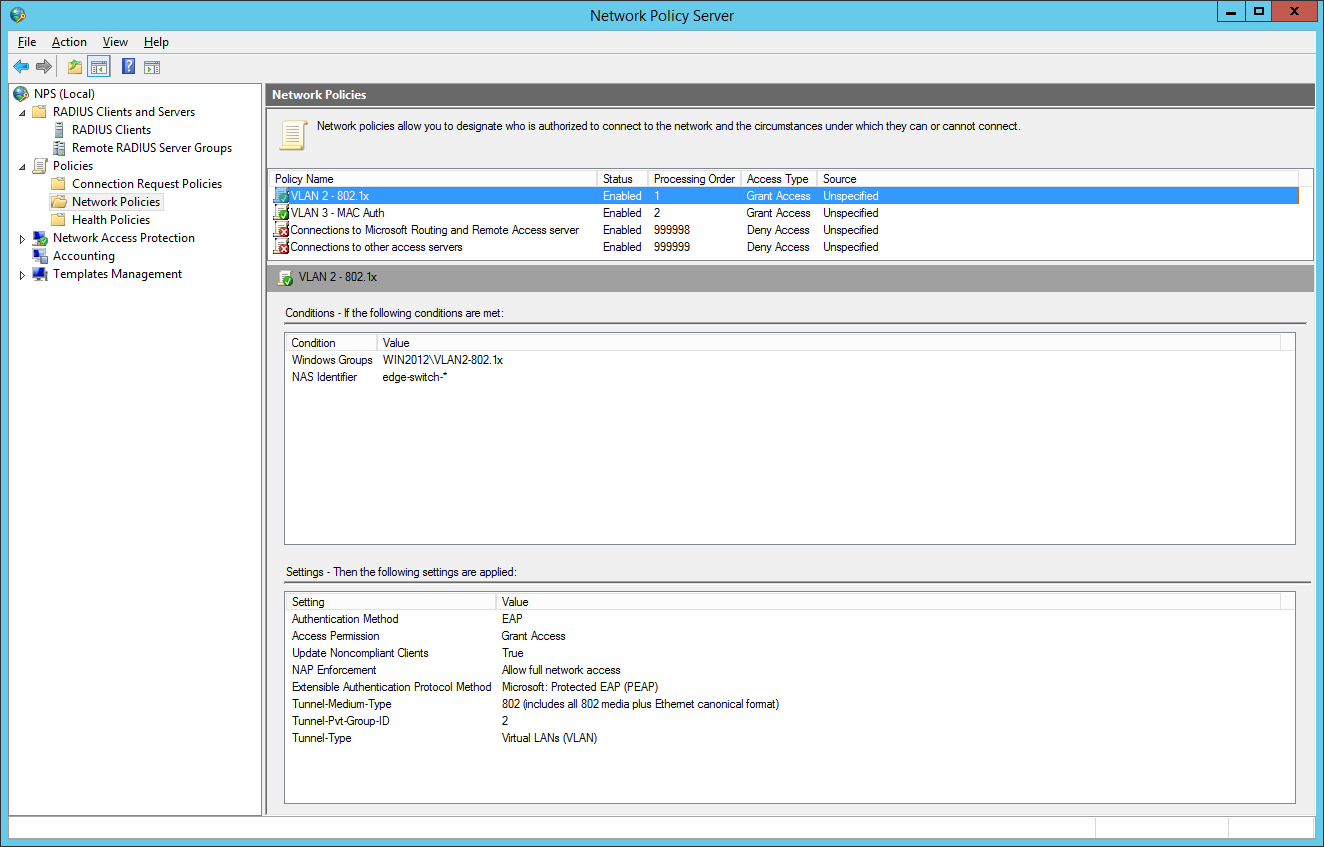
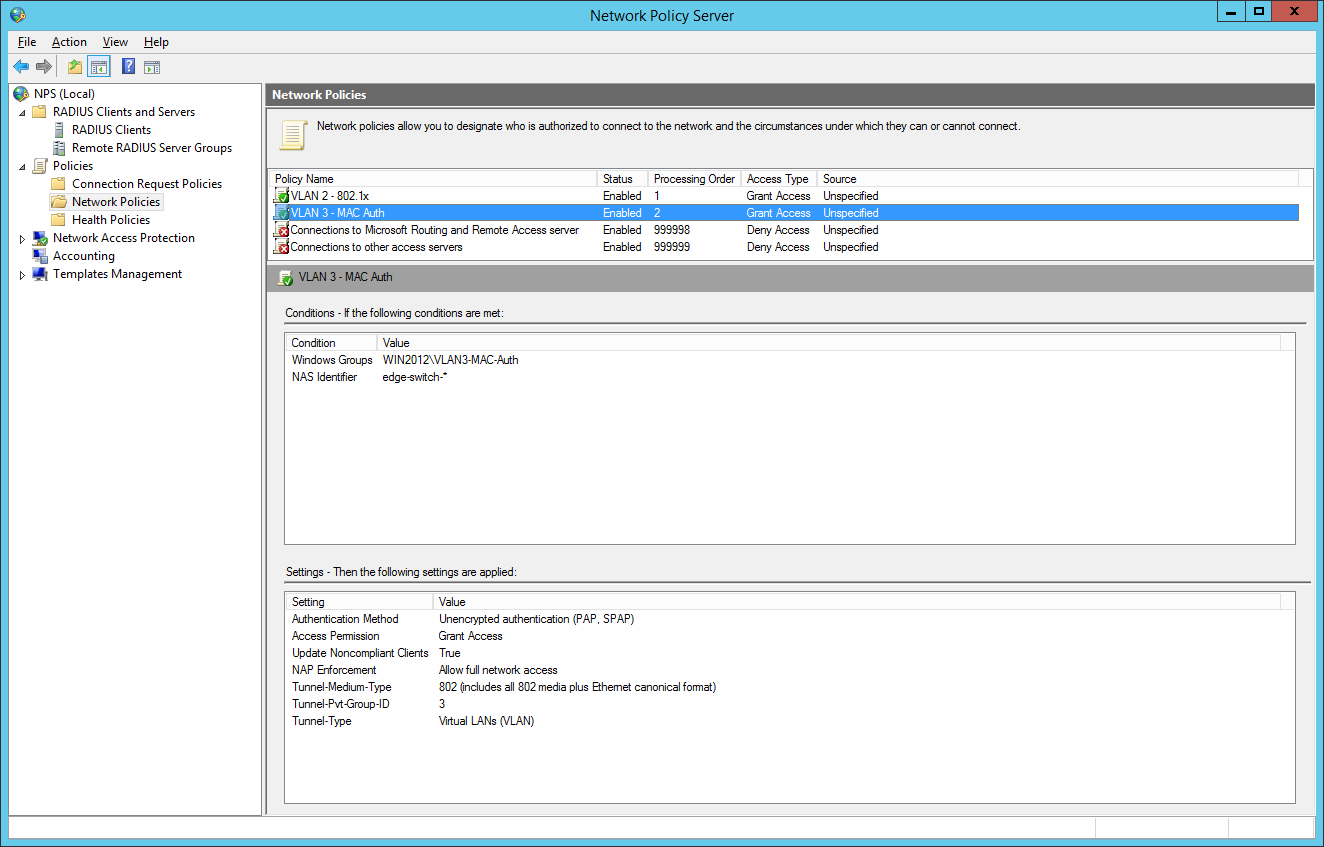
So we will now configure two network policies for our network access control:
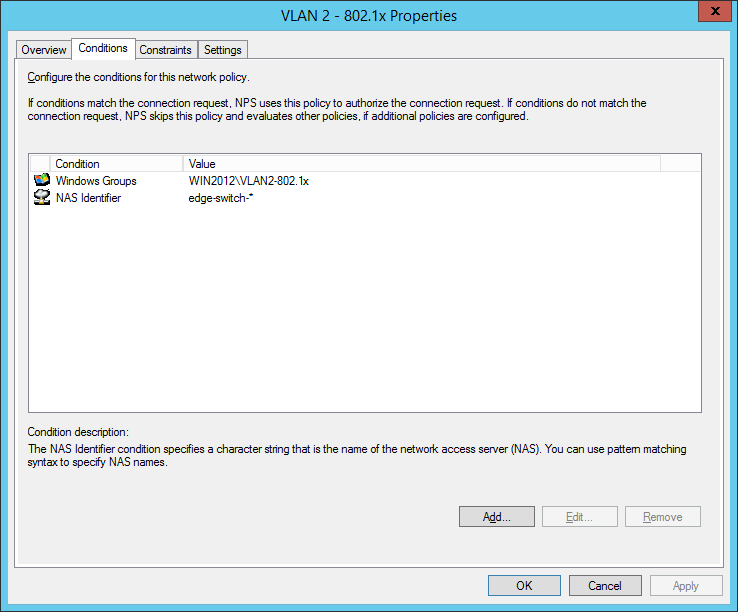
I also configured a NAS Identifier so no other device can use the radius server. The clients will use their computer certificate so you will need a running internal certification authority. Choose PEAP only as the authentication method:
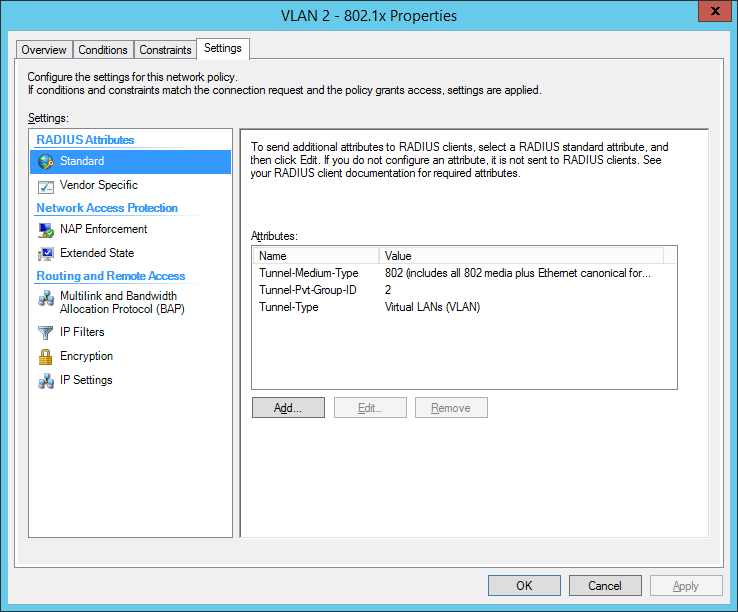
the next step is for our dynamic VLAN assignment. Dot1x devices are bound to VLAN 2:
the final dot1x configuration in the NPS:
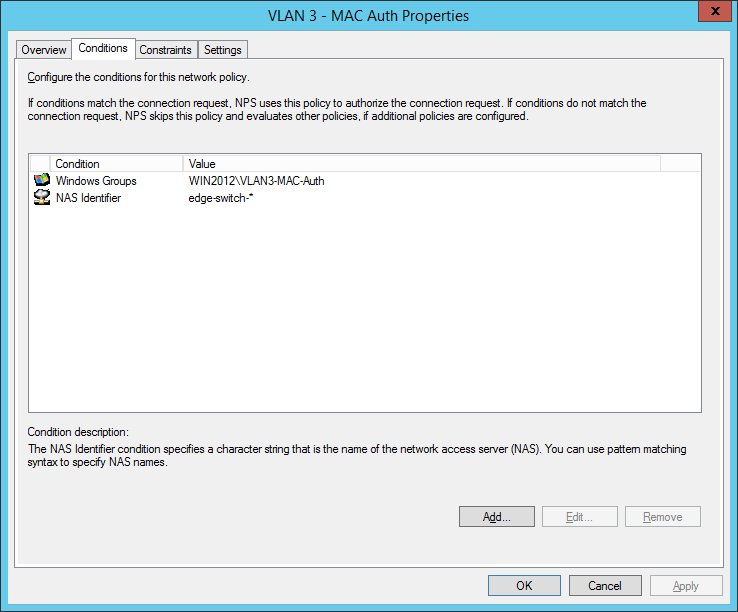
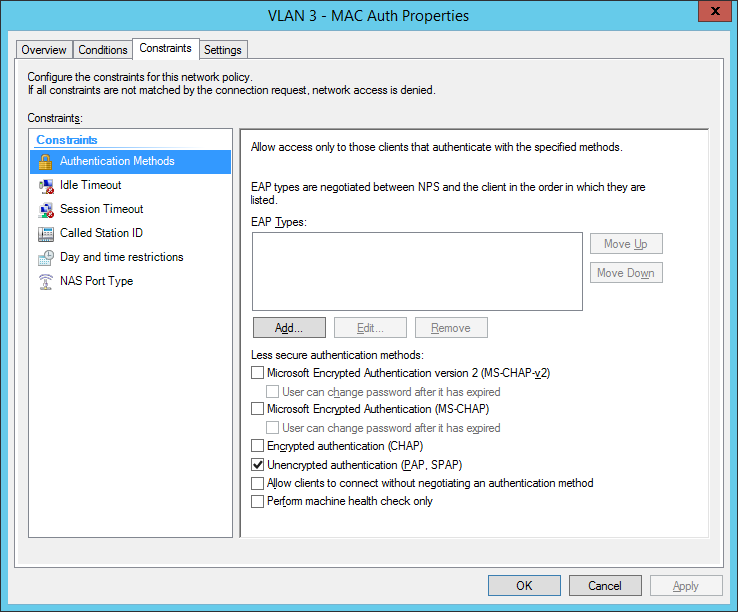
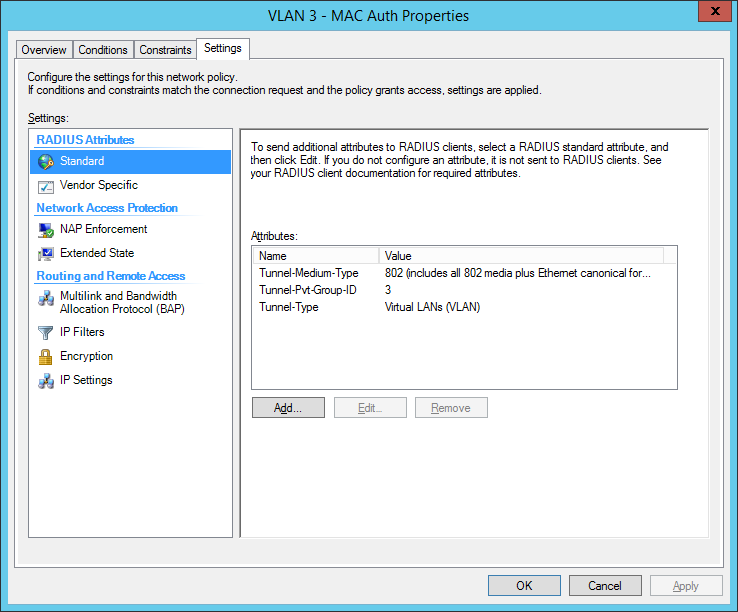
the second network policy is for the mac-based authentication:
Comware switches are sending MAC-Auth-requests via PAP (maybe you know how to change it to CHAP):
final MAC auth profile:
for now we have built up our authentication server. Now let’s go to the switch configuration. You have global configuration parameters and parameters for each interface. The best way is to use interface-range command to be safe at your configuration. Users who cant authenticate, will be forced to VLAN 999 (quarantine VLAN with no gateway). Here are the global parameters with explanations inline:
dot1x authentication-method eap # port-security enable # radius scheme MyRadiusServer primary authentication 192.168.0.1 key simple ***** primary accounting 192.168.0.1 key simple ***** secondary authentication 192.168.0.2 key simple ***** secondary accounting 192.168.0.2 key simple ***** accounting-on enable user-name-format without-domain # domain mycompany.local authentication lan-access radius-scheme MyRadiusServer authorization lan-access radius-scheme MyRadiusServer # domain default enable mycompany.local # vlan 2 name clients # vlan 3 name printers # vlan 999 name quarantine
now we will configure the interfaces:
Added 2 entries
interface range GigabitEthernet1/0/1 to GigabitEthernet1/0/48 port link-type hybrid port hybrid vlan 1 untagged mac-vlan enable stp edged-port poe enable undo dot1x handshake undo dot1x multicast-trigger dot1x unicast-trigger dot1x re-authenticate server-unreachable keep-online mac-authentication timer auth-delay 10 mac-authentication re-authenticate server-unreachable keep-online mac-authentication host-mode multi-vlan undo mac-authentication offline-detect enable mac-authentication parallel-with-dot1x port-security port-mode userlogin-secure-or-mac-ext loopback-detection enable vlan 1 to 4094 loopback-detection action shutdown
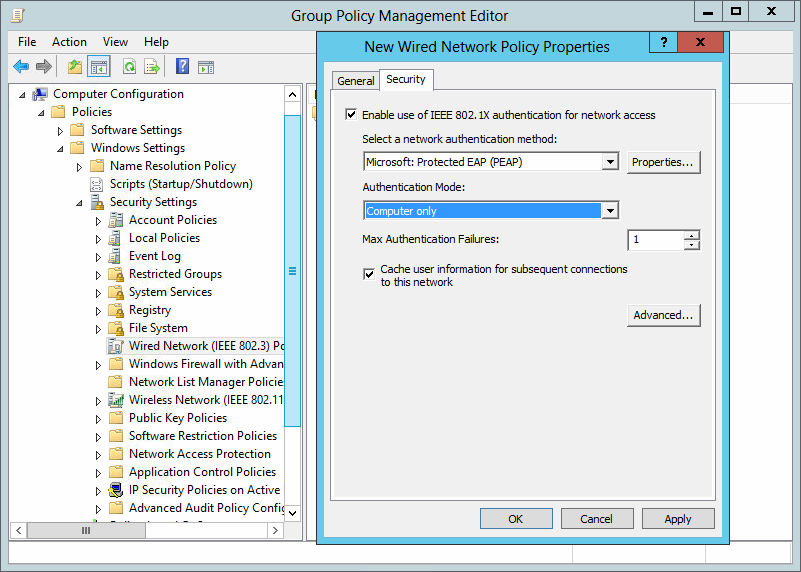
the last part is to configure all windows clients to send 802.1x auth data to the cable network. I’ve done this via a global group policy. You can find the settings under Computer Configuration / Policies / Windows Settings / Security Settings / Wired Network (IEEE 802.3) Policies:
So how does a working 802.1x-auth looks like?
%Jan 3 01:59:59:531 2013 edge-switch-01 DOT1X/6/DOT1X_LOGIN_SUCC: -IfName=GigabitEthernet1/0/10-MACAddr=0023-2415-42a3-AccessVLANID=1-AuthorizationVLANID=2-Username=host/PC123.mycompany.local; User passed 802.1X authentication and came online.
Successful Mac-Authentication of a printer:
%Jan 3 01:31:28:782 2013 de-pad-l19-edg01 MACA/6/MACA_LOGIN_SUCC: -IfName=GigabitEthernet1/0/9-MACAddr=0017-c82d-e9bf-AccessVLANID=1-AuthorizationVLANID=3-Username=0017c82de9bf-UsernameFormat=MAC address; User passed MAC authentication and came online.
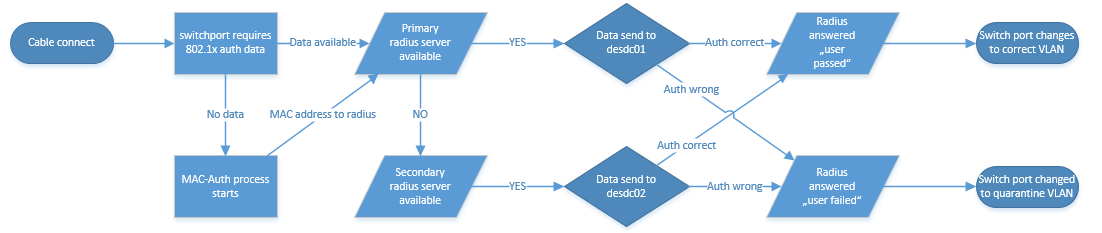
I tried to draw a flow chart which shows the authentication process, I hope it’s ok for you :)
Do you have questions? Feel free to write them into the comments and I will try to answer.
Have a nice and sunny day!
/edit: If you can’t see success and failure events, follow this instruction: NPS / Radius Server is not logging
/edit 2018-05-14: I corrected the global and interface configuration, we had problems with the old configuration









12 Responses
Thanks for this, I need to setup dynamic VLAN assignment in the near future but for Juniper equipment.
This at least gives me a good starting point, thanks for the write up.
Many thanks for the perfect tutorial on How to use 802.1x/Mac-Auth and dynamic VLAN assignment. Many of us can take help from it. Really nice.
Hey Mike,
Nice write-up. This was a great starting point for configuring the base for dynamic polices. Thanks!
Best,
Mike
hi Mike,
how ‘s about hybrid port with voice-vlan?
does it work?
thanks
Tung Duong
Hi Tung,
we had several problems with this config, currently we are investigating hyprid ports with “port security” command. I will update this post if we have prooved this version.
Can you tell me why I would do this over conventional static VLANs? What are the benefits radius dynamic VLANs?
Hi Andrew,
we have customers which want to divide the network for clients, printers and “special devices”. So you have different group/radius-policies to directly place the devices in the right VLAN. Dynamic VLAN is only a bonus feature which you can use. Of course, you can use only the 802.1x and Mac authentication for security purpose.
Hi.
I’m on the desktop side of things, so apologies if I use any incorrect terminology here.
Our Infrastructure team are looking at introducing 8021x in our schools.
They have a test setup where all 8021x devices pick up a data centre VLAN regardless of which building they’re in – eg 10.100.50.
Each building WIRED has its own unique IP – SchoolA=10.120, SchoolB = 10.130 and so on.
I’ve asked if the 8021x setup can be where 8021x devices in SchoolA will get 10.120.50; SchoolB will get 10.130.50
This would allow us to easily determine which building LaptopA actually is, in the same way as we can with our wired desktops. It also saves on SCCM boundary issues causing applications/updates to be pulled over the WAN rather than the LAN.
It’s been suggested that this may not be possible. Could someone confirm this?
Thanks in advance.
Hello! This is of course possible!
My idea (with examples):
SchoolA=10.120 (Location: Chicago)
SchoolB=10.130 (Location: Dallas)
So at Chicago you will have VLAN 333, every device is getting an IP address with 10.120.x.x. At Dallas every device in VLAN 333 is getting an IP address with 10.130.x.x. So the VLAN ID “333” is the same at every school but the DHCP scope and default gateway has it’s own address. So the device is getting the VLAN 333 at every location but another IP address. It’s very simple.
It’s not working if all schools are connected via Layer2 so VLAN333 can’t be a “standalone VLAN” at each geographical location.
Ask me any questions, I will try to help you.