Good day everyone!
If you want/have to implement wireless networks in companies you need to secure them more than your home WLAN. In this case, you need to use a radius server for this (so called WPA-Enterprise or WPA2-Enterprise Authentication with Protected EAP. I will use a Microsoft NPS (network policy server) on a Microsoft Windows Server 2016 OS. This is my test environment:
- NPS Server 192.168.91.23
- aruba IAP-205H 192.168.91.201
- aruba IAP-205H 192.168.91.202
- aruba Virtual Controller IP 192.168.91.200
- SSID “Networkguy-Office” with authentication of computer-group “Domain Computers”
- SSID “Networkguy-BYOD” with authentication of user-group “GL_WLAN-Access-BYOD”
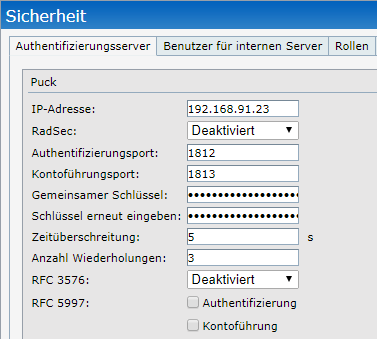
I combined the aruba access points to a virtual controller and configured the radius server “PUCK” under “Security”. The presharedkey secures the connection between the AP and the NPS:
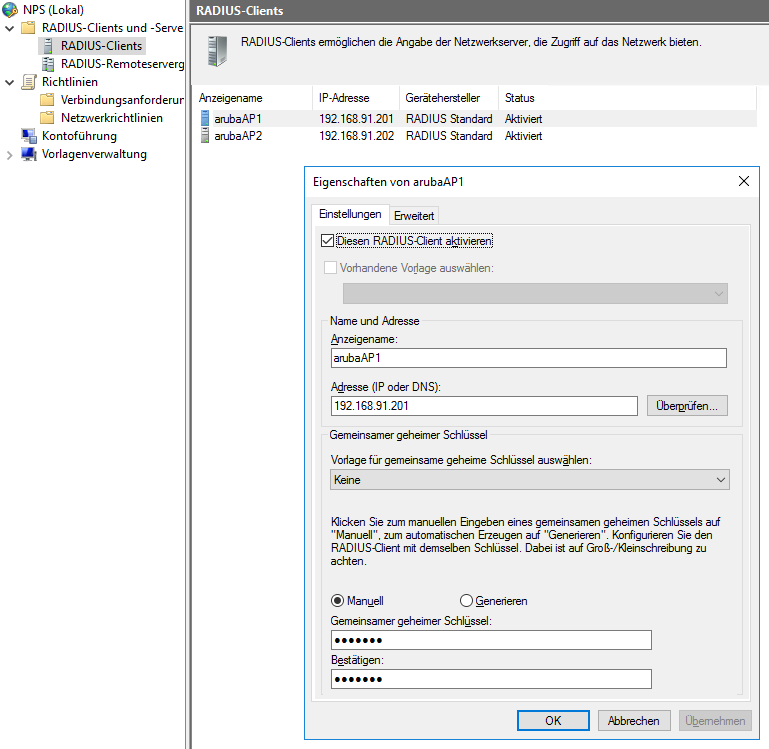
configure the WLAN controller or the instant access points as Radius Clients on the NPS:
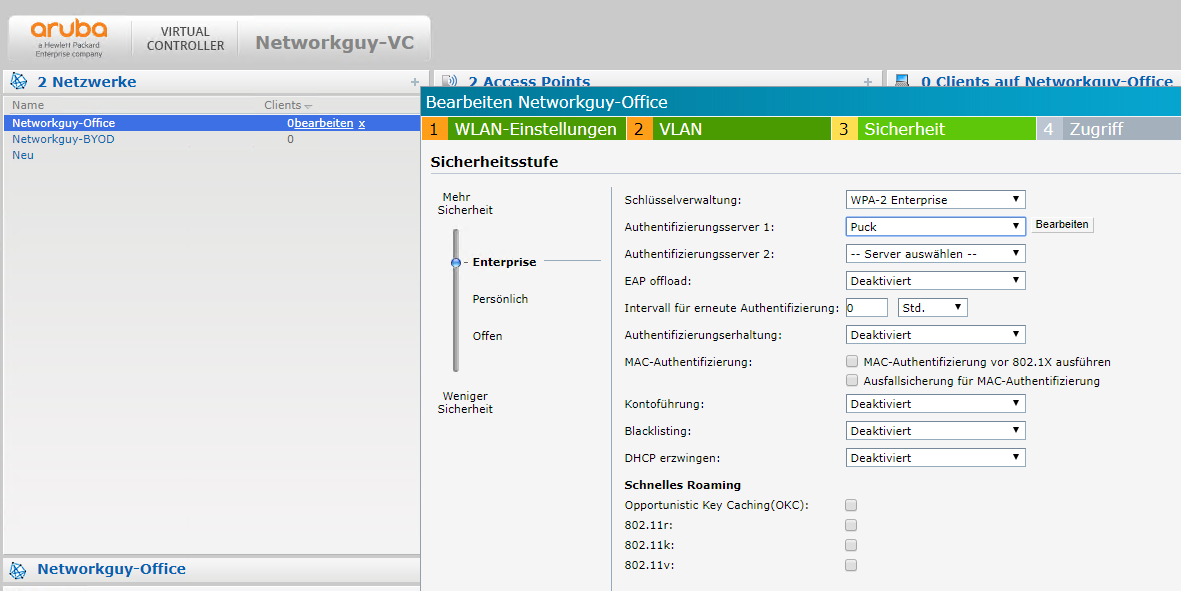
choose WPA2 Enterprise in your SSID options:
do differ the SSIDs at the authentication, we need to manually configure the called-station-id at the aruba virtual controller. Cisco Aironet WLCs do this automatically. To configure the called-station-id, we need to connect via SSH to the virtual controller IP address because you can’t configure this by GUI. We will use a colon as the delimiter:
00:0b:86:fe:31:da# configure terminal We now support CLI commit model, please type "commit apply" for configuration to take effect. 00:0b:86:fe:31:da (config) # wlan ssid-profile Networkguy-BYOD 00:0b:86:fe:31:da (SSID Profile "Networkguy-BYOD") # called-station-id include-ssid delimiter :
00:0b:86:fe:31:da (SSID Profile "Networkguy-BYOD") # end 00:0b:86:fe:31:da# commit apply committing configuration… configuration committed.
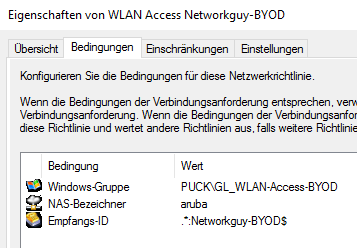
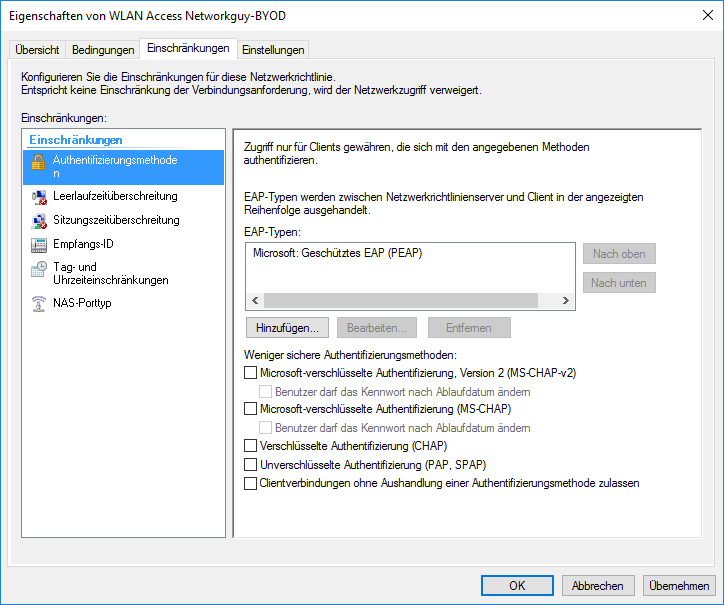
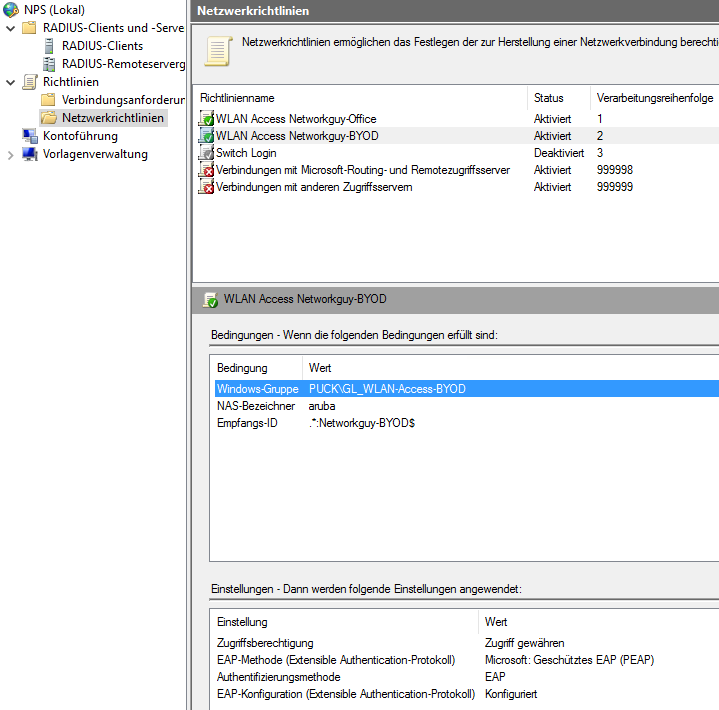
now we can configure the NPS rules. I used “aruba” as a NAS-identifier and .*:Networkguy-BYOD$ as the called-station-id. Change “Networkguy-BYOD” with your SSID name:
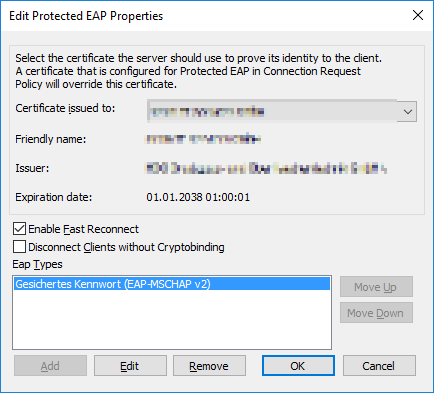
your NPS server needs an computer-auth-certificate, typically from the Domain Root Certification Authority:
our Bring your own Device (BYOD) policy is ready.
You can now configure your computerbased-auth policy. I always configure a network for all domain computers with access to internal LAN and a “Bring your own device” WLAN for employee-devices with internet-only access based an an active directory group.
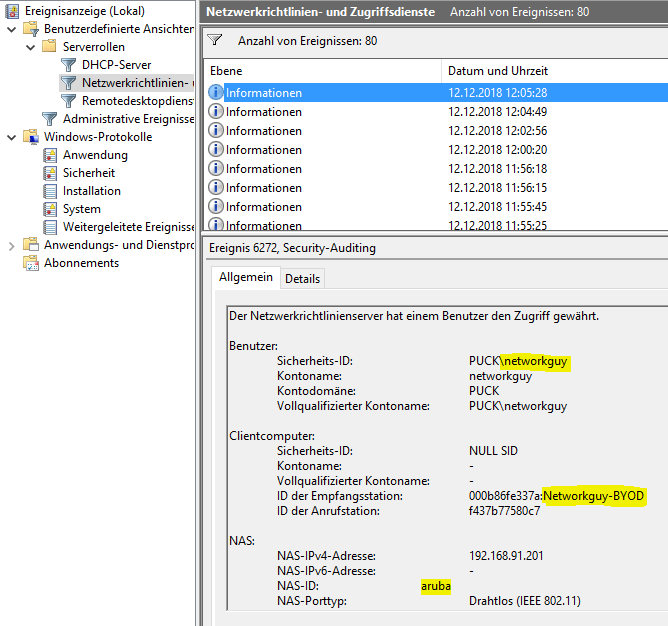
I connected my iPhone to the “Networkguy-BYOD” WLAN with success:
Feel free to ask in the comments. Have a nice day :)