Did you ever asked yourself how the web protection workflow is working within the Sophos UTM? Many customers have problems to understand the way the proxy works. The proxy can be used transparent (man-in-the-middle for http/https) or by “standard” where you use the proxy within your browser or WPAD. The proxy differentiates requests by source, person and time.
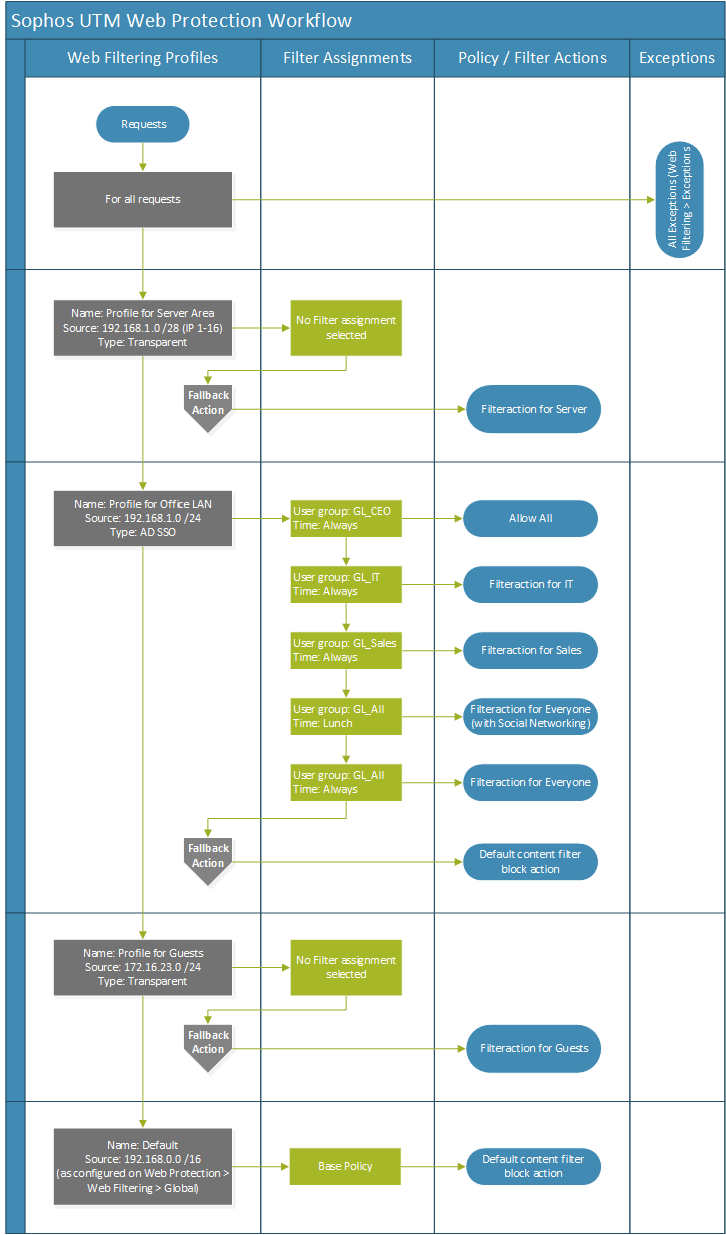
Here is a workflow graphic I made:
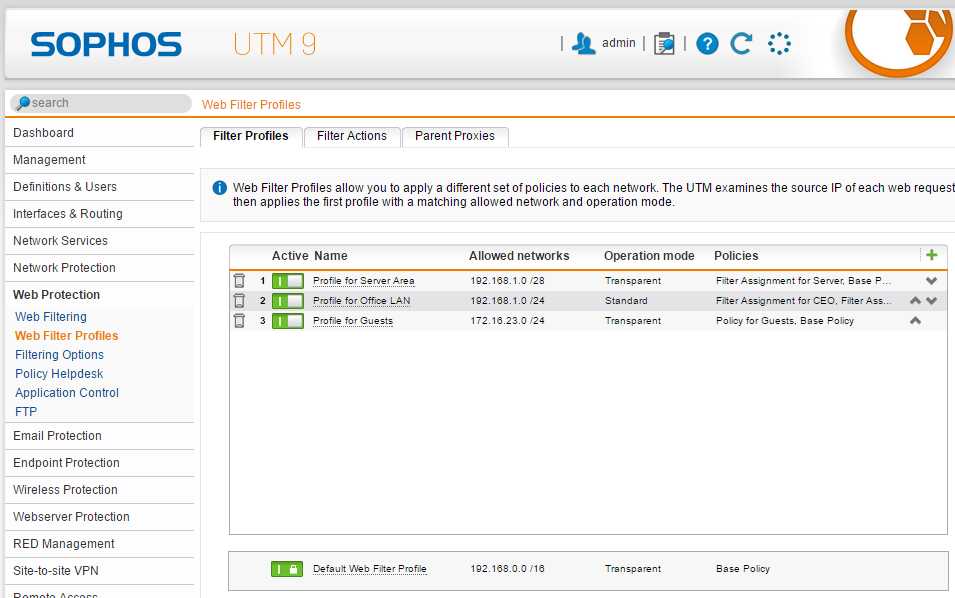
this is a workflow of one of my basic configuration for my customers. But how did it look like in the Sophos UTM WebAdmin? I configured a virtual test appliance with the names and settings like above to make it clearer:
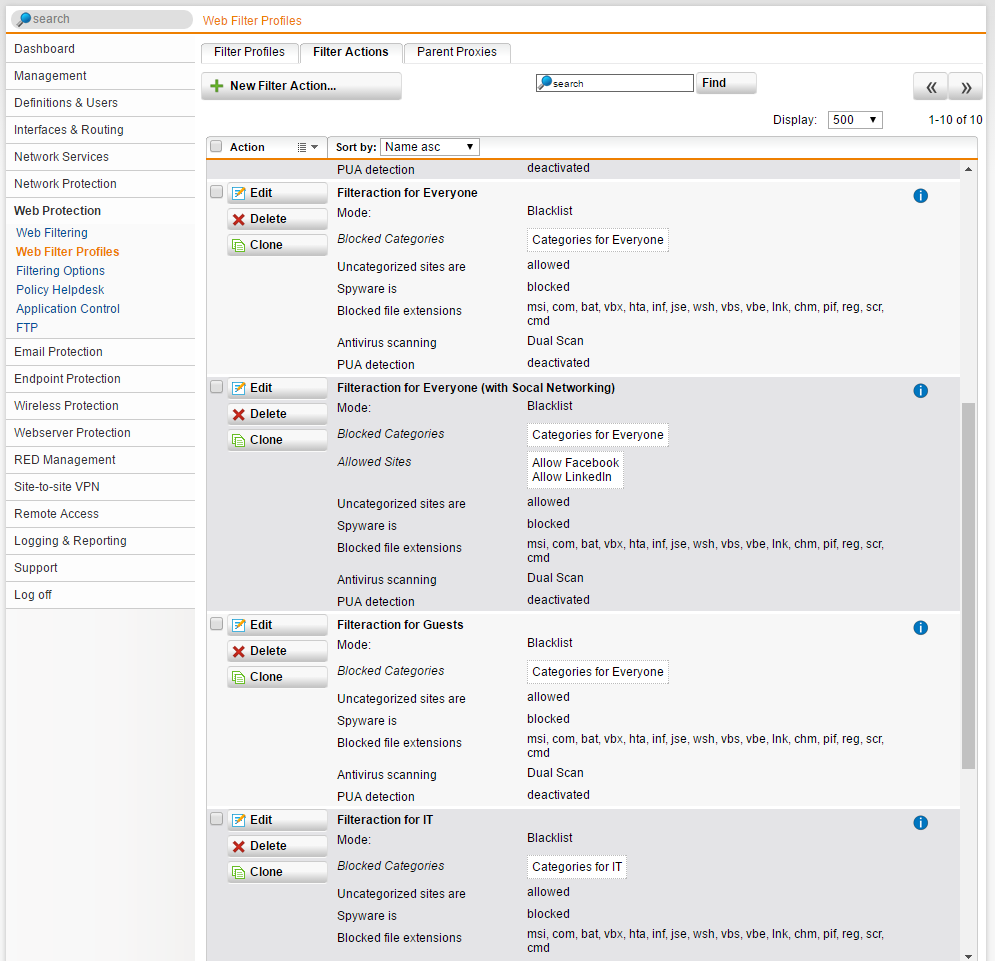
Profile for Server Area:
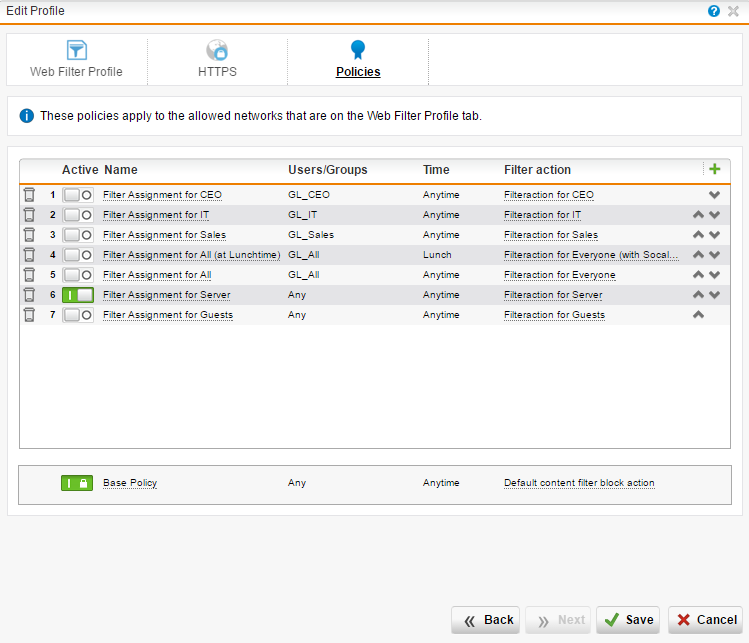
Profile for Office LAN:
Profile for Guests
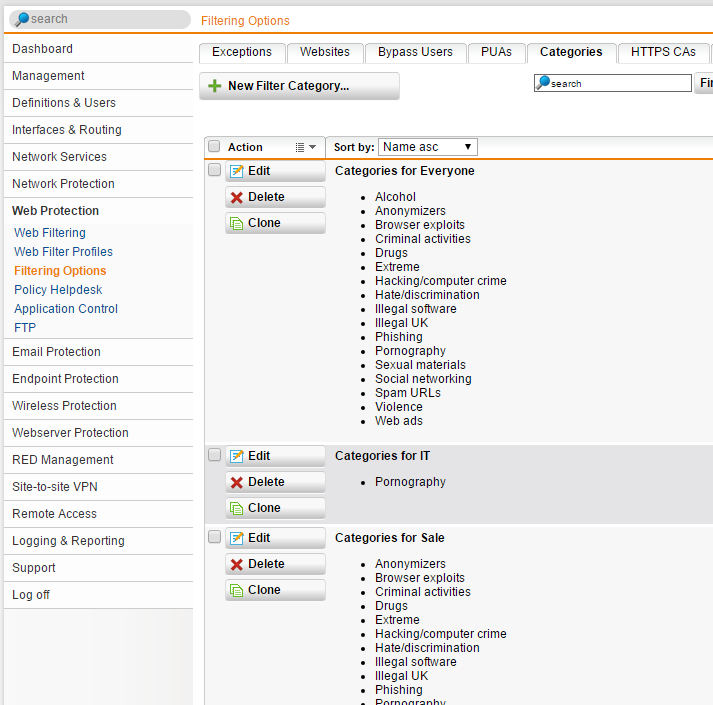
I always configure new categories for the groups /purpose:
I recommend to configure from “behind to ahead”: Categories > Filter Actions > Filter Profiles. Here are my filter actions for this example:
- Example 1
- Server “CustomerDC01” with IP 192.168.1.12 wants to update the Windows OS (http requests to update.microsoft.com)
- HTTP connection will be grabbed and allowed through the proxy because of global exception entry
- Server “CustomerDC01” with IP 192.168.1.12 wants to download SAP files from the internet
- Connection will be grabbed, scanned for malware (transparently, no proxy needed within a browser or system)
- Server “CustomerDC01” with IP 192.168.1.12 wants to update the Windows OS (http requests to update.microsoft.com)
- Example 2
- User “carl” (Member of GL_All and GL_FacilityManager) wants to access Facebook at 4 o’clock
- Browser says to proxy “please go to facebook for me” > Proxy blocked website (because social media is only allowed from 12 am to 1 pm)
- User “carl” (Member of GL_All and GL_FacilityManager) wants to access Facebook at 4 o’clock
If you want further examples, feel free to comment. Have a nice weekend! :)










2 Responses
Brilliant article!! ;-)
Nice work, mate! Really easy to understand.
Ah by the way. That nice workflow reminds me about the good old days when using Astaro.