In May I posted a tutorial for running a “router on a stick” with Cisco Router, Switch and HP Switch. Today I will show you to replace the Cisco Router with a Sophos UTM to route between different VLANs.
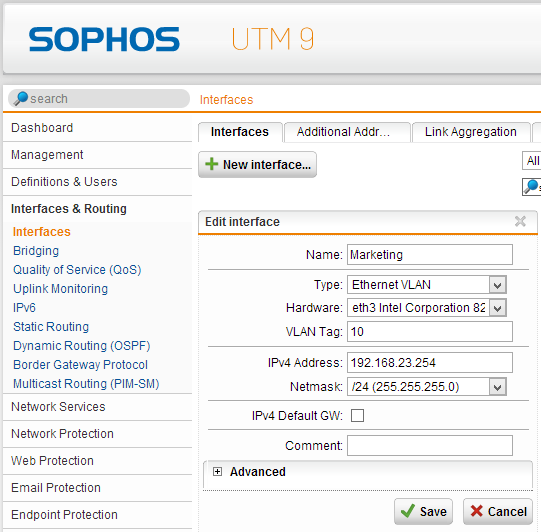
First we will connect a Sophos UTM interface (in our example eth3) with our switch environment (switch config example @ http://networkguy.de/?p=177). Now we can configure multiple “Ethernet VLAN” interfaces with a vlan tag like this (networks for marketing and sales):
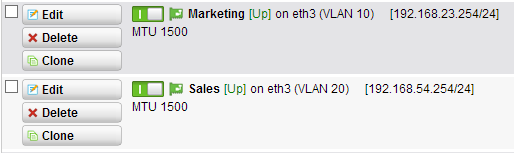
at the end of this you will see two new interfaces:
this will be the default gateways of those networks. You can configure a DHCP Server scope within the Sophos UTM or on your primary DHCP server with DHCP relay function at the “network services”. Keep in mind that you need to add marketing, sales and your servernetwork in the DHCP relay networks, otherwise no DHCP broadcast message is directed via unicast to your selected DHCP server.
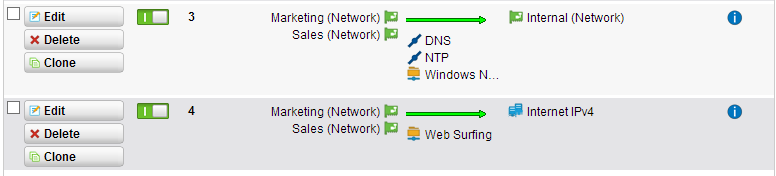
After this you can configure firewall rules like this:
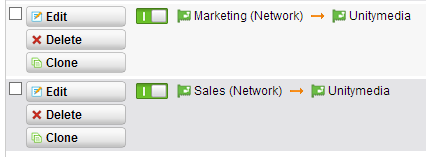
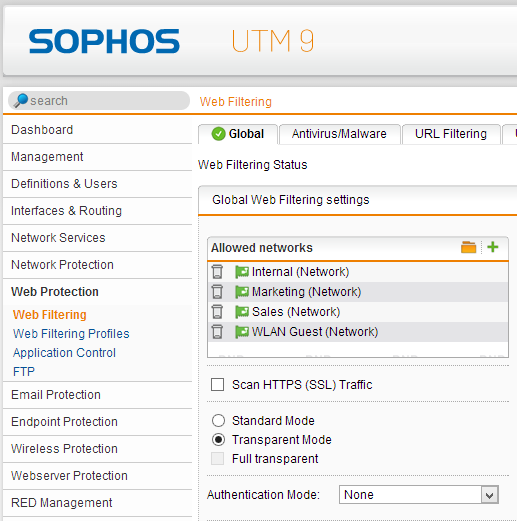
As the most firewalls, the Sophos UTM (based on a Linux OS; using iptables) is working with top-down-first-match. In our example I allowed Marketing and Sales network to use windows shares and make NTP and DNS lookups. To access the internet, I configured a rule that they can use Web Surfing protocolls to the internet. Use the network definition “Internet IPv4” and/or “Internet IPv6”. This definition means, that the can go through every interface that has a default gateway (mostly your WAN line). For accessing the internet you also need to configure NAT and secure them via Web Protection like this:
I hope I could cleary explain how to configure interfaces running on VLANs. You can use this mostly in case your Sophos UTM device hasn’t enough network ports.










29 Responses
It took me a bit, but setting up VLAN’s is pretty simple on the UTM. I basically setup VLAN interfaces on the eth0 port so the eth0 port is tagging all the VLAN’s I entered and then on the switch tag the same VLAN’s.
I don’t think there is a way to do untagged VLAN’s on a Sophos.
Gibts da nen Trick beim anlegen der Schnittstelle? Ich kann bei mir irgendwie bei Hardware nichts auswählen?
Oder benötigt man für die Aktion ne 3. nic?
Ich hab nen Router basierend auf deiner Hardware mit eth1 als Uplink und eth0 als Netzwerk und wollte nun nen Seperates Vlan fürs Wlan aufsetzen.
Switch ist nen HP 1810-24g
Du kannst ja deine interne Schnittstelle umändern auf “Ethernet VLAN” und VLAN Tag 1 (oder was du willst) eintragen und speichern, danach verlierst du den connect und musst auf dem Switchport auch das VLAN taggen, dann solltest du wieder draufkommen.
Dear Michel,
I believe this is the case when the sophos router takes care of the routing tasks, and the VLANs are actually created in a layer 3 switch.
How would be the case if we take care of the interVLAN routing on the switch.
I believe in that case we need some functionality like, allowing multiple subnets in a single interface.
I am making this assumption from the post here: https://supportforums.cisco.com/message/4178990
but the post does not apply totally to my case, because I don’t know how to configure Sophos router to do what the Cisco router does in the given link. (allowing multiple subnets).
Do you have a suggestion?
For example, you configure vlan 1 tagged and vlan 2 tagged on a switch port and you configure two interfaces with vlan tag in the Sophos UTM and plug the cable to the configured switch port. With that you have multiple subnets switched via vlan tagging on 1 port. It’s perfectly described in this post or am i wrong?
Are you asking if you can do the VLAN manipulation using your switches and still support more than one IP on the UTM? If so, then the answer would be yes. By using an Ethernet Standard IP on your internal interface and then adding additional addresses. (However, if you are handling the VLANs internally then one internal IP on the router should work just as well…)
Hi Michel,
Thanks for your answer.
Unfortunately, I am too new to this topic to be able to judge directly if you are right or wrong. However, here is one question which can help me find a solution: is the router performing the routing here or the Layer 3 switch? In my opinion it is the former case (not sure tho’). What is your take?
I’ll drop some more questions elsewhere in the forums and will come back if I have something clever to share.
Best,
D
Hi Michel,
I am receiving the “Duplicate IP address 192.168.0.1 from MAC 00:1a:8c:xx:xx:xx was detected on VLAN 200, port gi1/26″” message on my Cisco router, any idea why this might be happening?
The IP range of my VLAN 200 is 192.168.0.1/24, and I use the 192.168.0.1 IP when I create the VLAN interface on UTM for VLAN200?
This IP is also used as default gateway for the WIFI access point which is part of VLAN200!
Sounds like another device with the same ip address. Do you mean Cisco router or cisco switch?
Yeah I have a typo there: Cisco Layer 3 Switch, SG 500 – 28 port, running in router mode…
And my router/firewall is Sophos UTM
This IP is excluded from the DHCP pool that I have created at Cisco Switch so I believe it is not reserved by any device connected through the Cisco Switch. On port gi1/26 I have the trunk to the Sophos router for internet access. According to your setup you use the address of the VLAN to create the respective VLAN interface in Sophos, am I wrong?
The Switch needs to be in switchmode, not router mode. The Sophos UTM is connect with 1 cable to the switch. The Switch has tagged vlan100/vlan200, the Sophos UTM has two interfaces on eth0 with vlan tag on each. Look at this picture for better understanding:
http://networkguy.de/?p=177
(just exchange “Cisco Router” with “Sophos UTM”)
Are you coming from Paderborn? :)
Hi Michel,
I am eagerly trying to achieve the case where the sg500 switch (in router mode) does the inter vlan routing and takes away some of the routing load from the sophos utm. Anyways, if I am not able to achieve it the way I want, I will have to switch to the case which you have suggested: with the sg500 in switch mode.
Still can not find where does this duplicate IP occurs from, anyways.
Regarding to your other question, well, I can not say that I come from Paderborn, but I am located there at the moment. What is the rationale behind you question tho’?
Hi,
when you want to do the intervlan routing on the cisco device, you need to use the interfaces for routing and the utm is only the door to the internet. Here is an example: http://networkguy.de/?p=465 the utm needs static routes to the networks configured at the cisco device.
Short example:
cisco device:
vlan 100 with 192.168.100.1 /24
vlan 200 with 192.168.200.1 /24
vlan 23 with 192.168.23.1 /30
default route to 192.168.23.2 (your sophos utm)
sophos utm:
1 interface with 192.168.23.2 /30 with routes “192.168.100.0 /24 to 192.168.23.1” and “192.168.200.0 /24 to 192.168.23.1”
+ nat, firewall and web application rules for this networks
I see that you post from UNI Paderborn “eduroam” network :) I live and work in Paderborn at the “Technologie Park” near the University :P
Hi Michel,
Sorry for the late response, had some other priorities in meantime so had to switch tasks.
Lets see if I understand correctly your suggestion.
You create three different VLANs and you prefer to use VLAN 23 for internet conncetion? Am I correct? Then, what is the port VLAN membership. If guests are supposed to connect to VLAN 200, and they are supposed to have internet connection, then they have to be connected to VLAN 23 as well right? In other words, the ports that are going to serve the guests, have to be members of two VLANs, namely, vlan 23 and vlan 200? right? What is the tagging then? –> Tagged members for both VLANs?
What is the type of the interface that you create at the UTM with the IP 192.168.23.2 /30? Ethernet Static? Ethernet VLAN?
Thanks in advance for your response.
PS: I am rather surprised by the coincidence with the Paderborn stuff :D, which company do you work for?
I work for “neam IT-Services” :)
no you can’t have a device in both VLANs. Each VLAN has its own network and its own ports on a switch. You can route between them and can configure firewall rules (for example “VLAN 23 -> any -> Internet IPv4”. So VLAN 23 is not allowed to connect to VLAN 200. Here is an example of this: http://networkguy.de/wp-content/uploads/2012/05/router-on-a-stick.png
I am interested in paying consultant fees for remote (online) configuration support for a limited time design project. Either way (yes or no) if you are not interested — please let me know if you are open to this.
Hi, I’m trying to setup a couple of VLANs on a home network and am having a few issues.
Could I please ask what the NAT config is for and whats the Unitymedia interface is in the screenshot ?
Just trying to understand your setup and why you can’t just add the VLAN Interface directly into the web filtering network list. Many thanks,
Ian.
Hi Ian :)
the Unitymedia Interface is my provider, so it is the “WAN” interface. The configured interface with VLAN tag is called “MyNetwork (Network)”, it is a auto-generated non-deletable definition and yes, I just add it to the web protection networks.
Hi, Got it working. I hadn’t setup the masquerading rules for the VLAN’s so the packets were going out on the WAN with internal 192.168.x.x address and then not coming back. Your article pointed me towards the NAT area so thank you for the help.
Bought a cheap NETGEAR DS104 hub off ebay and hooked up a laptop and used NST Live CD and wireshark to figure it out. Also hooked it up after the switch and verified the VLAN tags. Quite interesting seeing the raw packets. (For a home network newbie anyway!)
Now got to sort out a VPN connection, keep me busy a bit longer…
dear sir
when i try to configure the other vlan and attach it to eth3 it doesnt show? the ethernet hardware assigned to the first vlan wont show up for the next vlans?
Yes it won’t show up with “Ethernet-Standard” but with “Ethernet-VLAN”, just change the type of the interface.
Good Day,
I’m new to Sophos UTM and did the same set up as above as testing. the difference is I am not connecting to the internet. What I wish to achieve is to connect the Marketing and Sales VLAN’s. But unfortunately was not able to succeed.
I am using the utm on virtual box. and connect to catalyst 3650 switch.
I have 2 nics on my host and works as bridge on the vbox sophos utm.
I had 1st nic to serve as eth0 – internal network
then 2nd nic to serve as eth1 – where I set the Ethernet VLANS (on your example this is eth3)
hope to have some advice regarding my set up.
Hi Emman,
the Cisco Switch has the default native vlan 1. I don’t know your VLAN numbers for marketing and sales. If you have vlan 10 and 20 you need to configure the switch like this:
interface GigabitEthernet 0/x
switchmode mode trunk
switchport trunk native vlan 1
switchport trunk allowed vlan 10
or you want to tag vlan 10 and 20:
interface GigabitEthernet 0/x
switchmode mode trunk
switchport trunk native vlan 1
switchport trunk allowed vlan 10 20
if you want to tag vlan 1 you can change the native vlan to a number that doesn’t exist as a VLAN.
I think your problem isn’t the Sophos UTM. Try to configure networks in virtual box (interface 1 = vlan tag 10, interface 2 = vlan tag 20)
and than you configure eth0 with marketing address and eth1 with sales address (no vlan tagging in Sophos UTM). How are you using virtual box? Is it on a linux machine or a windows machine? Virtual Box is a client VM-Tool like VMware Workstation or not?
In a vmware ESX server you just need to configure another vswitch with a vlan tag.
I used same VLAN numbers 10 and 20, same ip addresses as well. For the switch ports to be connected by other computers, i set native vlan 1 and allowed vlans 10 and 20 as I intend only to connect vlan 10 and 20.
Virtual Box is a client VM-Tol like VMware Workstation, and i think there might be some limitations.
I’m planning to have it tested on an actual Sophos UTM device probably by next week. I’ll try to see if my current configs work, it would probably be that Virtual Box is not ideal as a testing VM.
Hi Michel,
Hopefully I’m not to late to the party here but my best friend and I are new to Sophos and have been instead running pfSense for a while now. We have been trying to transfer our networks over to Sophos as it seems like it should be A. Easier to configure/manage and B. A more Feature rich environment.
Now in our networks in our houses we are running our own Active Directory with DNS, DHCP, Exchange,Web Server and a couple of other things thrown in there all virtualized using VMware ESXI and connected to a Cisco 3750 Layer 3 Switch along with our Access Points and the rest of the computers. Now throughout the network we have 7 different VLANs (none of which are vlan1) that are all being intervlan routed by the switch as its a layer 3 switch.
The problem that we’re running into is while all the VLAN’s are able to see the Sophos UTM, their not able to get through the UTM to the internet.
Any help is greatly appreciated.
Hi Jason,
do you have a firewall-rule with “Network A” -any-> “Internet IPv4” and do you have the NAT rule “Network A” -> “WAN-Interface”?
Hi Michel,
We do have both of those rules in place and we pretty much took everything that is there after the initial setup and replicated it for each of the vlans/subnets.