During a firewall migration at one of my customers, the IT director asks me If we can configure IPsec fallback for the branch offices. The remote devices are all from Bintec and there are over 30 branch offices out there. First, correct the NAT settings on all devices with this tutorial. I blogged it last year.
Now we will configure the remote Bintec device. Go to VPN/IPsec. This is an example, you can choose whatever you want:
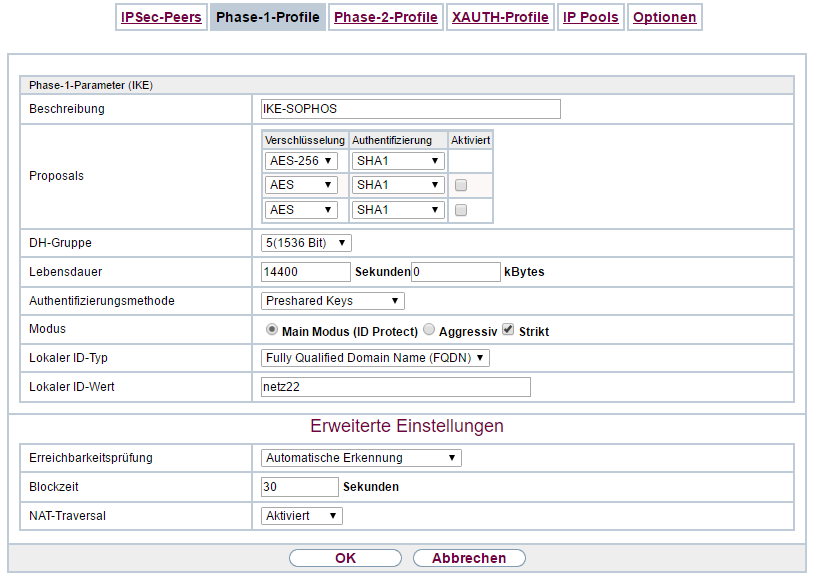
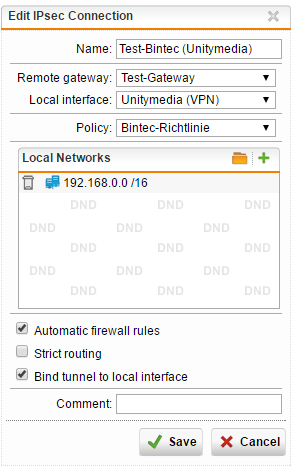
This is the main vpn setting:
this is the backup vpn setting:
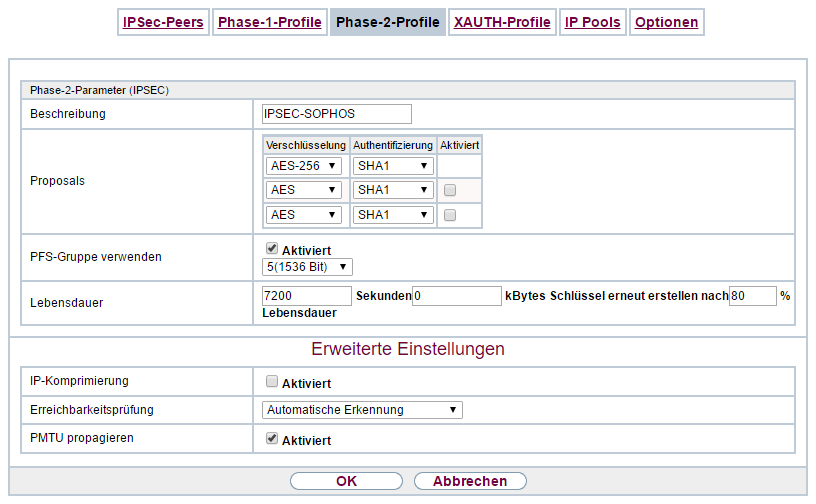
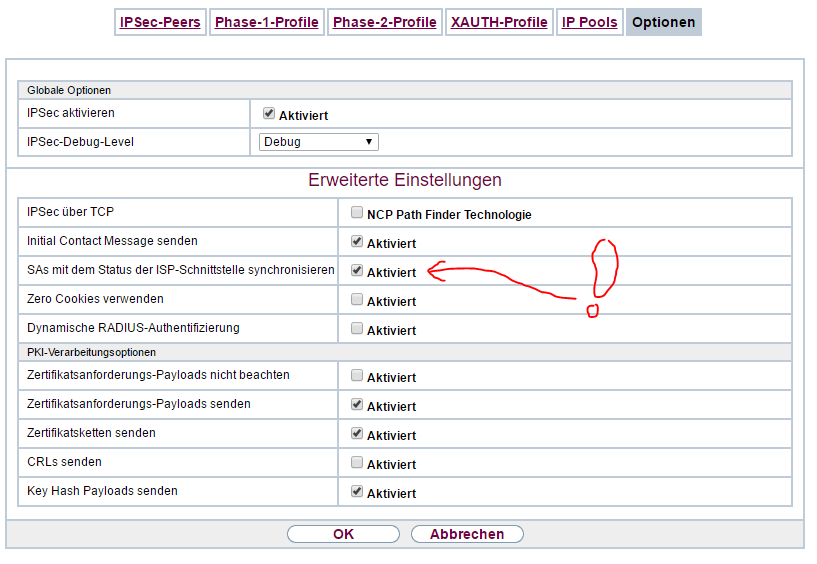
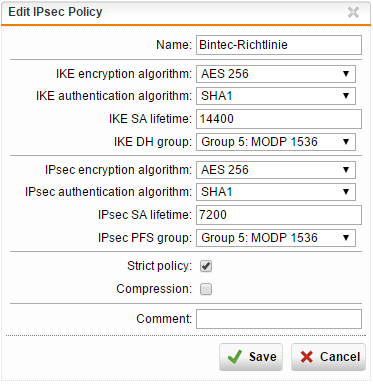
this is the configuration of the Sophos UTM:
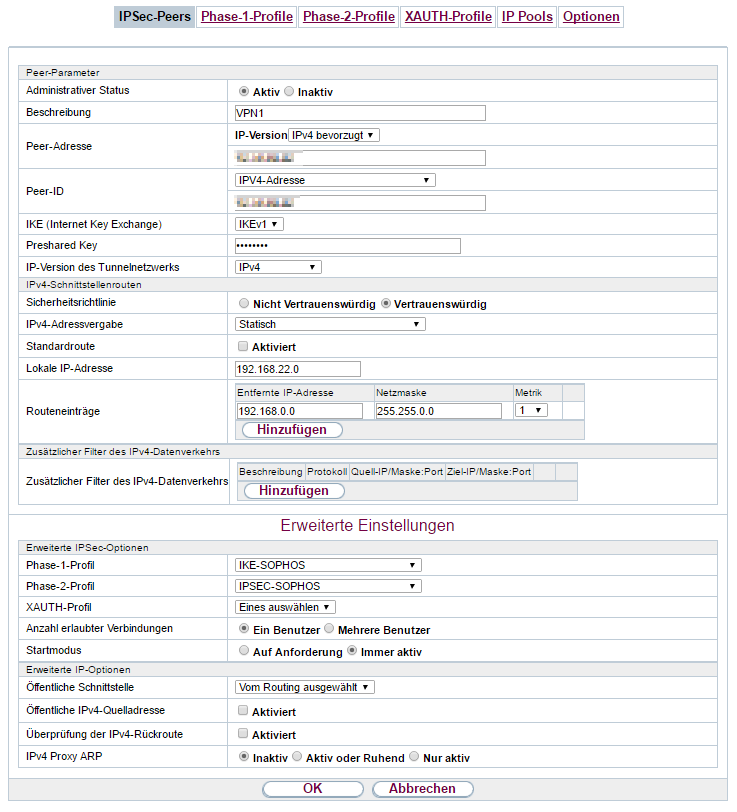
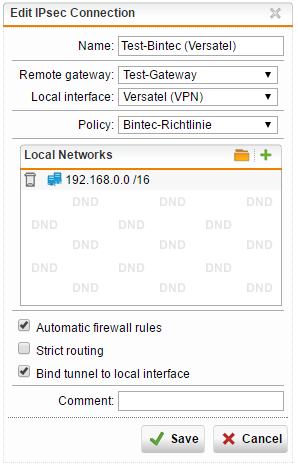
IPsec Policy:
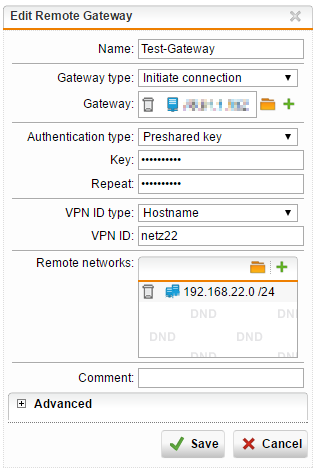
Remote gateway:
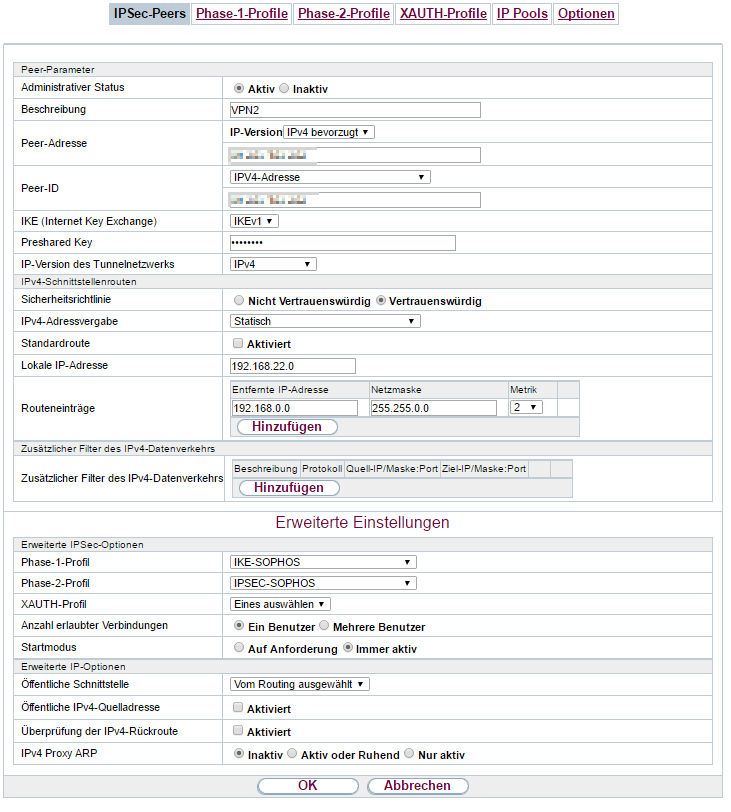
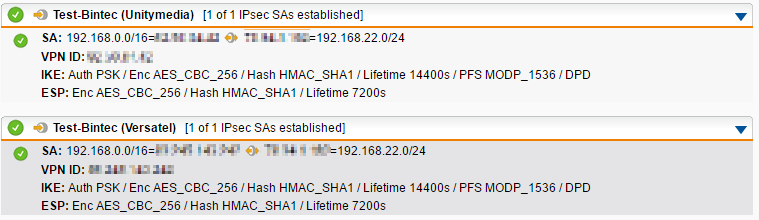
Main VPN over Unitymedia line:
Backup VPN over Versatel line:
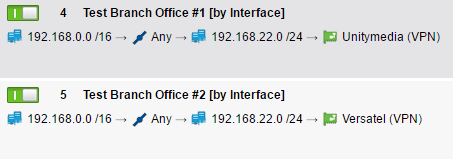
it’s important that you activate “Bind tunnel to local interface” because we will work now with multipath rules. Go to Interfaces & Routing / Interfaces / Multipath Rules and add two rules:
So the remote network 192.168.22.0 /24 is available over both WAN interfaces (by binding it to the interfaces):
If you disconnect the main line (in this example Unitymedia), the VPN stays active for over a minute. Have patient when you ping your remote device. After about a minute, your ping is getting back because both recognize that the main VPN tunnel is down and the multipath rule leads to the second line (Versatel). If the main line is back again, the first multipath rule gets active immediately.









2 Responses
Really nice! Will try this out in my lab with Cisco IOS as endpoint.
Hi Mase,
I’m really excited about this. Tell me if it’s working with Cisco IOS.