News
- Maintenance Release
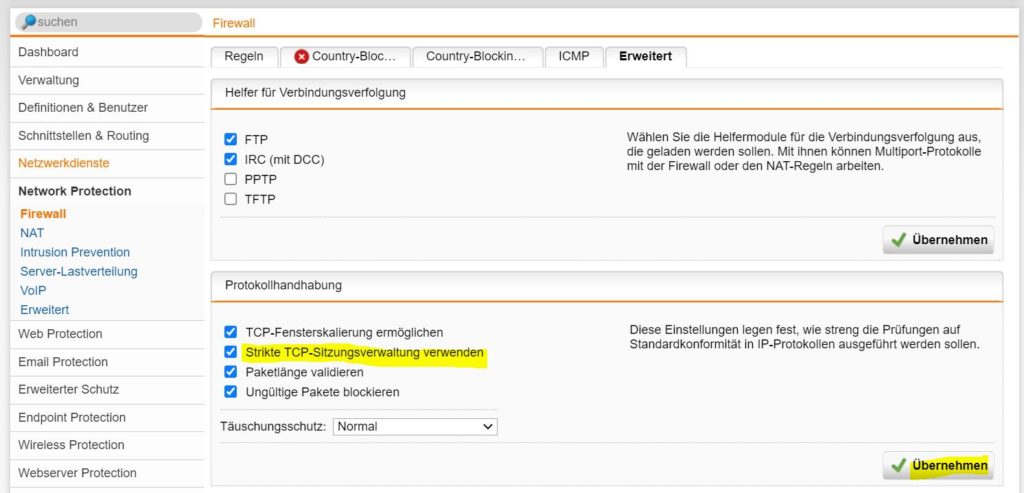
- Strict TCP Session Handling enabled by defaultNew installations of UTM 9.706 have strict TCP session handling enabled by default.
When updating to 9.706 and strict TCP session handling is not enabled, admins can enable it under Network Protection > Firewall > Advanced. - Secure Up2DateUp2Date updates will be downloaded via HTTPS connections. In cases where UTM 9 is being used with an upstream proxy or behind a different firewall, it may be necessary to change the configuration on these devices to allow UTM 9 to retrieve Up2Date information via HTTPS.
- Email Protection anti-spam engine changed to Sophos Anti-Spam Interface (SASI)Starting with this release, E-Mail Protection will use the Sophos Anti-Spam Interface (SASI) for anti-spam scanning. SASI is already being used as part of Sophos Email and will replace the currently used anti-spam engine in UTM 9.
In case of false positive or false negative detections, please follow the instructions in this support article on how to submit a sample.
How to activate Strict TCP Session Handling
Remarks
- System will be rebooted
- Configuration will be upgraded
- Connected REDs will perform firmware upgrade
- Connected Wifi APs will perform firmware upgrade
Issues Resolved
- NUTM-12050 [Access & Identity] IPv6 auto-firewall rules missing with IPsec S2S respond only
- NUTM-12062 [Access & Identity] AD Group object not updated when user with an Umlaut in the username logs in
- NUTM-12188 [Access & Identity] openl2tp service is dead and unable to start
- NUTM-12198 [Basesystem, UI Framework] Webadmin host injection reported
- NUTM-11753 [Basesystem] SG450 RAID status not alerting
- NUTM-11988 [Basesystem] Interface goes down after re-assigning the hardware of an interface
- NUTM-11989 [Basesystem] BGP issue causes long delay in UTM startup
- NUTM-12064 [Basesystem] Perl – Vulnerabilities
- NUTM-12112 [Basesystem] Libc Vulnerabilities
- NUTM-12122 [Basesystem] net-snmp Vulnerability CVE-2019-20892
- NUTM-12354 [Basesystem] Patch BIND (CVE-2020-8620 CVE-2020-8621 CVE-2020-8622 CVE-2020-8623 CVE-2020-8624)
- NUTM-12471 [Basesystem] OpenSSL: CVE-2020-1971 – DoS
- NUTM-11941 [Email] unnecessary SMTP restarts due to a SSL VPN login
- NUTM-12286 [Email] ECC Ciphers ECDH-ECDSA not supported by Exim SMTP
- NUTM-12542 [Email] Arbitrary Config Object Deletion via User Portal</Fix>
- NUTM-11915 [Network] Ipsec routes will be removed if a wifi network will be added and the ipsec local networks overlap with an existing wifi network
- NUTM-12045 [Network] INFO-122 Dhcpd not running
- NUTM-12280 [RED] RED site-to-site tunnels reconnecting at random intervals (utm to tum)
- NUTM-12253 [RED_Firmware] Split DNS doesn’t work with SD-RED
- NUTM-12379 [RED_Firmware] RED doesn’t reboot after reconnect doesn’t work properly
- NUTM-12098 [UI Framework] Remote crash of User Portal index.plx
- NUTM-11950 [WAF] AH00051 child pid XXXX exit signal Segmentation fault (11), possible coredump in /tmp
- NUTM-12148 [WAF] WAF not always sending SNI to backend
- NUTM-12029 [Web] AWS https scanning connect timeout on some sites with chrome
- NUTM-12204[Web] High CPU with http proxy coredumps.
- NUTM-12032 [Wireless] “&” sign in PSK cause issues after config change
- NUTM-12127 [Wireless] wireless client list empty
- NUTM-12254 [Wireless] Website not loading for wireless user due to large packets whose size is larger than the MTU of the link
- NUTM-12362 [Wireless] AP55/55C/100X/320X : Communication issue for Clients which are connected to the same SSID but at different APs
- NUTM-12383 All SSIDs disappears from AP and disconnects all connected clients
Download
https://download.astaro.com/UTM/v9/up2date/u2d-sys-9.705003-706008.tgz.gpg