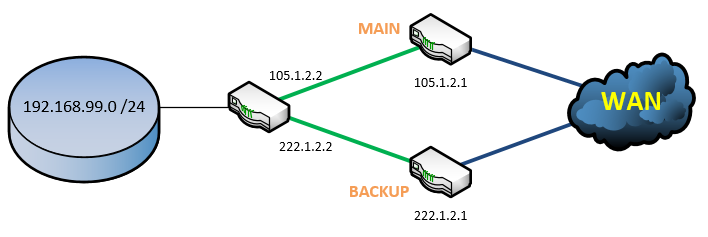
You can configure redundant internet lines with Cisco routers. For this we will use route tracking. The configuration of this is also for backing up your VPN lines. In this example we have to internet lines: The main line is 105.1.2.x and the backup line 222.1.2.x (I also bound a crypto map to it):
interface Vlan2
description Main Provider Line
ip address 105.1.2.2 255.255.255.252
no ip unreachables
ip nat outside
crypto map CompanyMapinterface Vlan3
description Backup Provider Line
ip address 222.1.2.2 255.255.255.252
no ip unreachables
ip nat outside
crypto map CompanyMap
We will configure a fixed route to the Google DNS Server 8.8.8.8 (you can choose another public server for reachability if you want) to ping this server always over the main line:
ip route 8.8.8.8 255.255.255.255 105.1.2.1
now it’s time to configure the tracking of the Google server:
ip sla 10
icmp-echo 8.8.8.8 source-ip 105.1.2.2
timeout 1000
threshold 2
frequency 3ip sla schedule 10 life forver start-time now
now the Cisco router is pinging the device. I always ping a server in the internet, because the provider router can be reachable but the internet line not. It’s also better for use with Dialer-Interfaces. In this case you will use “source-interface DialerX” instead of “source-ip”. To see if the script is working, you can view the statistics for this:
Router#show ip sla statistics
IPSLAs Latest Operation StatisticsIPSLA operation id: 10
Latest RTT: 56 milliseconds
Latest operation start time: *10:16:15.581 UTC Tue Mar 17 2015
Latest operation return code: Over threshold
Number of successes: 67
Number of failures: 0
Operation time to live: Forever
We will track the reachability of this ping script. On new Cisco router models (Cisco 886 for example) you will use:
track 10 ip sla 10 reachability
older devices like Cisco 876:
track 10 rtr 10 reachability
To use both lines active-standby you will need to configure two default-routes to the internet. One with the tracking of the main line and one fixed route with a higher administrative distance:
ip route 0.0.0.0 0.0.0.0 105.1.2.1 track 10
ip route 0.0.0.0 0.0.0.0 222.1.2.1 200
So if the tracking is not working (ping to 8.8.8.8 over main line) the second default-route will be used. To configure a redundant NAT, we will use route-maps for this:
ip access-list extended NAT-ACL
deny ip any 10.0.0.0 0.255.255.255
deny ip any 172.16.0.0 0.15.255.255
deny ip any 192.168.0.0 0.0.255.255
permit ip 192.168.99.0 0.0.0.255 anyroute-map WAN-LINE-1 permit 10
match ip address NAT-ACL
match interface Vlan2route-map WAN-LINE-2 permit 20
match ip address NAT-ACL
match interface Vlan3ip nat inside source route-map WAN-LINE-1 interface Vlan2 overload
ip nat inside source route-map WAN-LINE-2 interface Vlan3 overload
to make a real fallback test I would recommend to pull out the main line and try to access the internet or your VPN location. In case you are using IPsec VPN, keep in mind to configure both peers and presharedkey for the second WAN line in your headquarter. VPN is only loosing one ping packet, internet access (surfing websites) is direct available, in some cases the NAT needs to change to the second line but this only tooks about 5-10 seconds in my case. If you have any further questions feel free to ask in the comments.
I wish you a nice sunny day :)








