- Advanced Zero-Day-Protection
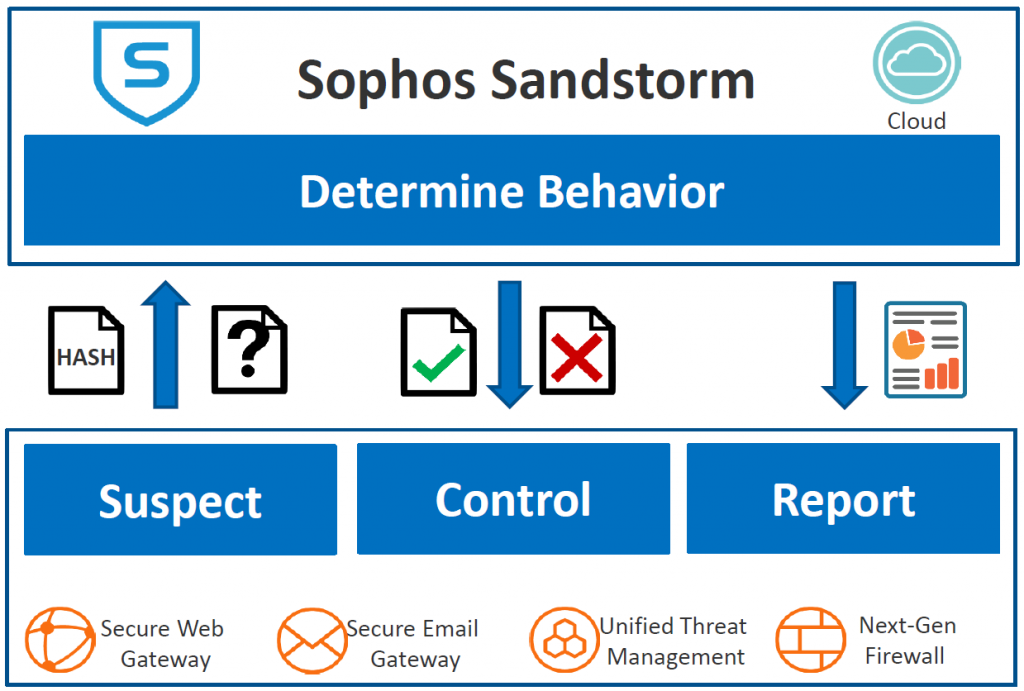
The Sophos Sandstorm (“Breach Detection Platform”) is a dynamic-cloud-technology for scanning files on different OS and browser versions to detect zero day malware. The product FireEye for example is a on-premise solution for this. Sophos centralized this into a cloud-system.
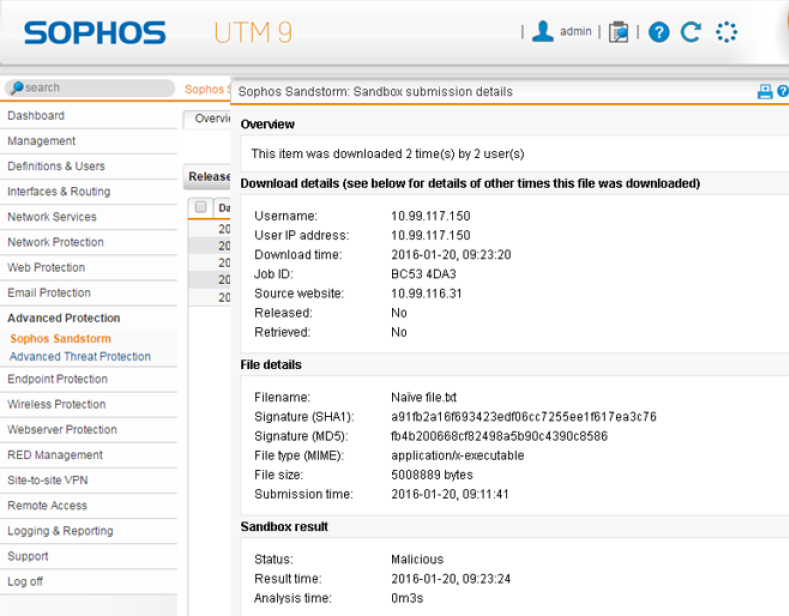
The popular zero day malware “Locky” is a normal executable or macro script which download files from the internet. Anti-Virus-Engines doesn’t recognize them as malware. Locky downloads other tools to encrypt your local files and data on network shares. Locky is mutating everytime he is spreading himself, so there is also always a new hash value for the file. Sandstorm analyses every download or mail-attachment within a fast cloud architecture. The files will be send encrypted and deleted after the analysing. The access to the file will be forbidden if the file is doing malware stuff like Locky. Every file gets a hash value, so already analysed files can be directly forbidden or allowed. The function is an additional subscription and not included within the Full Guard / Total Protect subscription. General Availability will be April this year. Sophos Sandstorm is now ready to us for the standalone web and mail appliance from Sophos.
How Sophos Sandstorm Works:
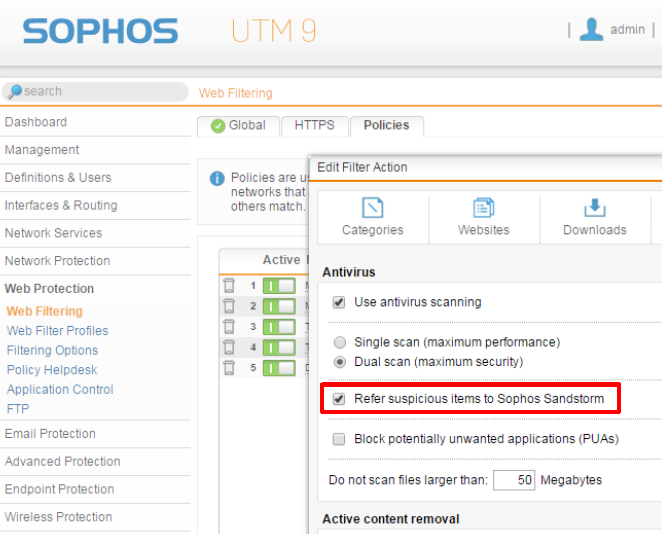
The configuration of the sandstorm feature is very easy, just activate the licensed feature in the web and mail protection:
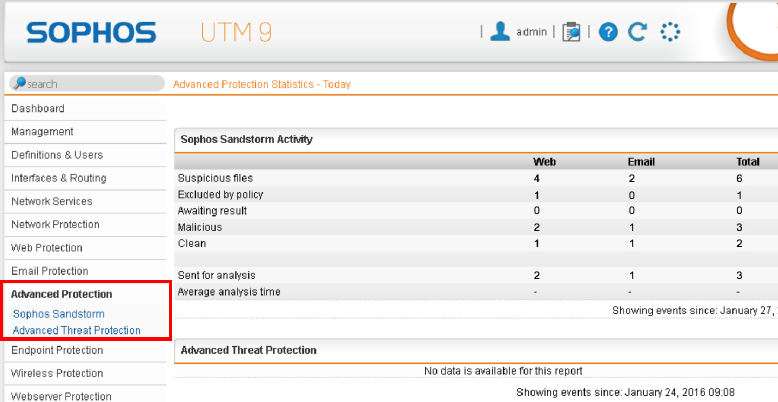
The reports can be viewed under “Advanced Protection”:
If you want to test the new 9.4 Beta, you can download it here.
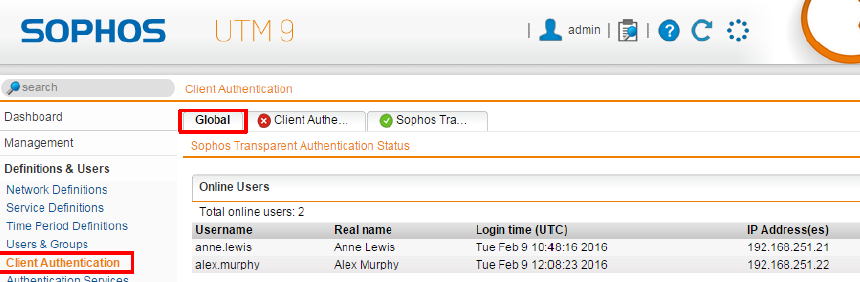
- Sophos Transparent Authentication Suite (STAS)
Finally a tool running on a domain controller to auth user machine logons. It’s now easier to configure user-based rules within the firewall and the application control. It was already possible in the past but you need to install the client auth tool on every PC. The STAS collects logon events and transmits them to the UTM. User-Auth for terminal server use is in work.
Additional UTM news:
- WAF Persistent Session Cookies
- Persistent cockies was one of the most wanted features. You can now publish your sharepoint and you won’t get an auth box on every item on the page. It has also a better collaboration with webserverfarms.
- IPv6 SSL VPN Support
- Sophos Access Point AP15C
- AP with ceiling deployment
- 2,4 OR 5 GHz
- Supported at UTM version 9.4
- Sophos RED15w
- 802.11n WLAN (2,4 OR 5 GHz)
- 2×2:2 MIMO
- available at March 2016
- Sophos SG85/SG85w
- low-cost-model for small/home offices
- same case as SG105/115 but without VGA port
- 8GB flash onboard
- no on-box reporting (Recommendation: Free iView variant)
- only Sophos AV
- WiFi-Modell with single radio (2,4 OR 5 GHz)
- 4x 10G SFP+ Flexi-Port Module
General Sophos news:
- Sophos released a test website to test malware scanners or web-category access: sophostest.com
- Sophos will release their “Sophos Threat Analysis Centre” at the end of this year. They’re also planing an API for this. The analysis centre is a portal where you can analyze malware. At the end you will get a report with all informations (downloading modules, writing files and registry keys, etc.)
- Project Leibniz defines a cloud-based WiFi management like Cisco Meraki. The audience can also be customers who “rent” the WiFi from their service provider (multi-client capable).
- Sophos Cloud will be renamed to “Sophos Central” (I think cloud was a misnomer ^^)
- Sophos
CloudCentral Firewall Manager (online webinterface to manage customer UTMs/XGs) - Sophos SafeGuard HTML 5 auto-encrypt
- SafeGuard can now encrypt “on-the-fly” if you want to send confidential information to a person via Mail. SafeGuard encrypts the complete file to a html5 container file protected with a password. The receipient opens the html file, enters the password and can download the protected file WITHIN the html. A very
nicesexy feature!
- SafeGuard can now encrypt “on-the-fly” if you want to send confidential information to a person via Mail. SafeGuard encrypts the complete file to a html5 container file protected with a password. The receipient opens the html file, enters the password and can download the protected file WITHIN the html. A very
Feel free to comment if you want more detailed information.










One Response