Some weeks ago one of my customers first WAN IP (used for mail-out) was listed in a spam blacklist. SMTP internet-traffic was only allowed for the mailservers and there was no deny-packet for tcp 25 in the network logs. So I thought a bot used an Outlook client for spaming but I was wrong. Spamhaus.org XBL said, that the entry comes from cbl.abuseat.org:
One hour after the blacklisting, clb.abuseat.org said, that this IP is infected with ZBot:
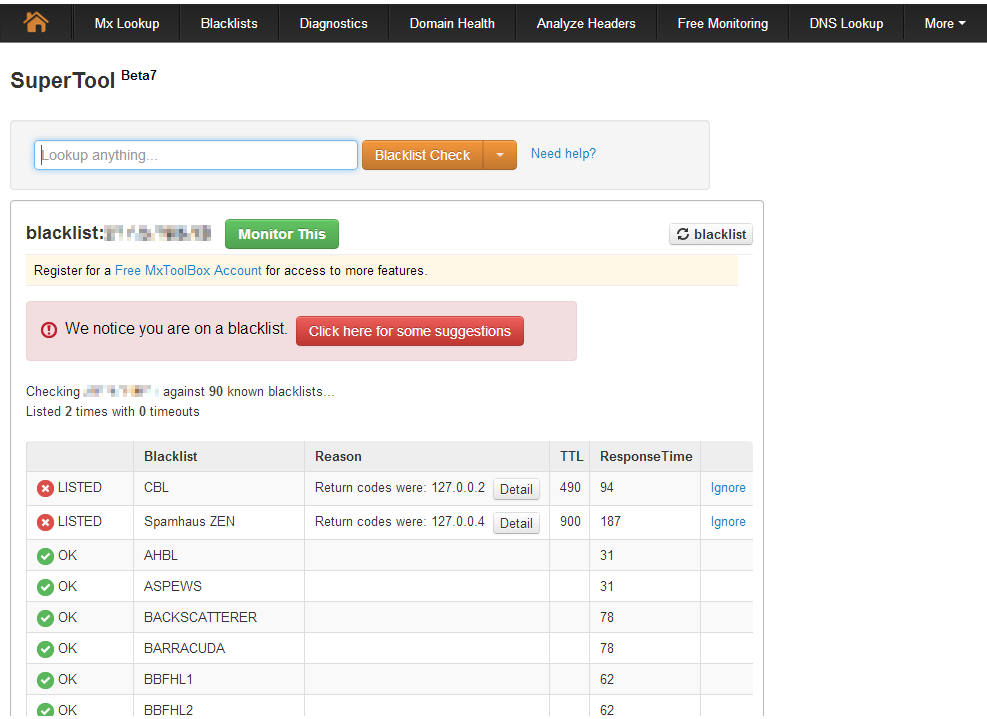
There were going connections to IP 87.255.51.229, a sinkhole for the ZBot. When you do a reverse DNS lookup you will see the name entry “this-domain-is-sinkholed-by.abuse.ch”. So this IP was once ago a real ZBot Command and Control Server (C&C). The provider or Spamhaus changed this to a sinkhole to find infected devices who are connecting to this IP. The server receives the packets like “Hello I’m a infected ZBot client, please tell what I have to do” but the server replies with a “connection refused”. After this, the sinhole tells spam-blacklists that the source IP of the packet is infected with Zeus Bot and your IP will be listed in a blacklist. To make this more visual, I made a Visio drawing:
I searched via shell command for the IP 87.255.51.229 in the packetfilter.log placed in /var/log/:
more /var/log/packetfilter.log | grep 87.255.51.229
with this command, we found the infected notebook. You can remove the ZBot / Zeus Bot with Norton Power Eraser, but the better solution is to reinstall the complete operating system. You can finde more information about the ZBot here at the Symantec website.










5 Responses
Hi, We are currently looking for a UTm and Sophos is on the shortlist. But why doesn’t the UTM detect this and block the outgoing packets? This would the perfect Use Case for a UTm vs classic Firewall or not?
Hi Guido,
no it can’t be recognize because it was a normal http request so there was no malware code within the tcp stream.
Hi Guido,
i think this packets will be blocked with the Advanced Threat Protection (ATP) in Version 9.2 coming March/April this year.
Yes, i wonder why only now… Fortinet seems to do this for a while already (4 Years) :)
Not sure yet what to choose…
Traffic with virus-infection is detected by Sophos UTM already, but we are speaking about malware, that communicate as a normal PC (for example a normal http connect to a server). Sophos UTM will be able to see this with hashes coming from the central Sophos cloud to recognize such traffic.