Hello Guys,
Today I am going to talk about a problem with my company’s wildcard certificate.
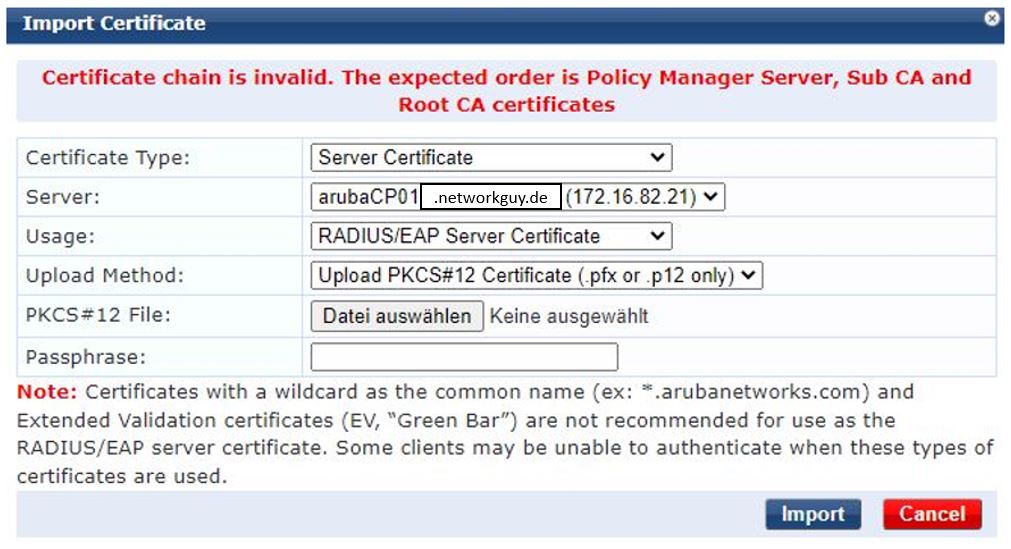
Because I wanted to display the Clearpass captive portal without certificate errors. I tried to import our company wildcard certificate. And in doing so, I encountered the following problem:
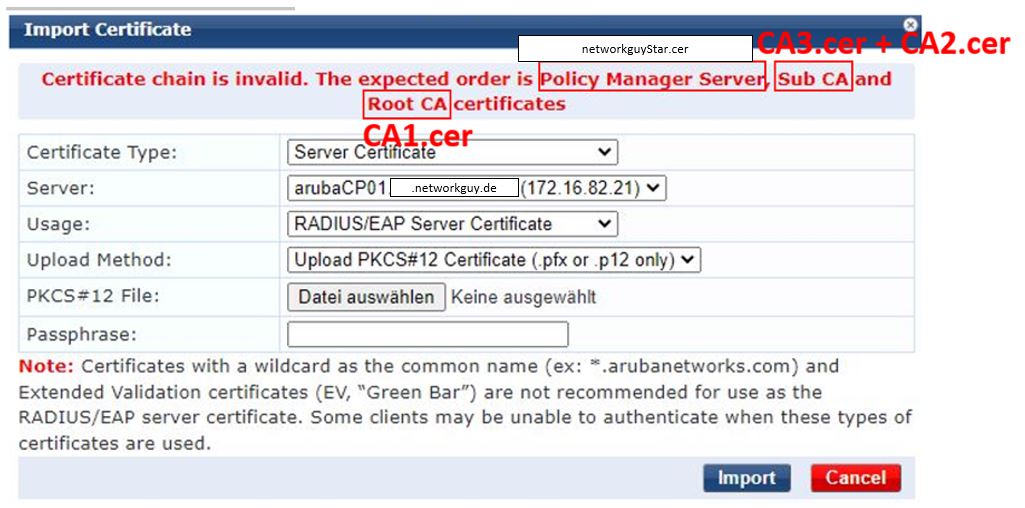
Here we have the problem that the certificate chain for the Clearpass is in the wrong order. Many systems like the Aruba Mobility Controller or Sophos SG don’t seem to care if the chain goes from root to server certificate or from server certificate to root CA. But not the Clearpass :D
The solution
The only thing that helps here is to rebuild the certificate chain. First, we need the root CA and all sub CAs. The easiest way to get this is from a system where the wildcard certificate is already integrated. For example, the Sophos SG Firewall.
extract the root and sub CAs
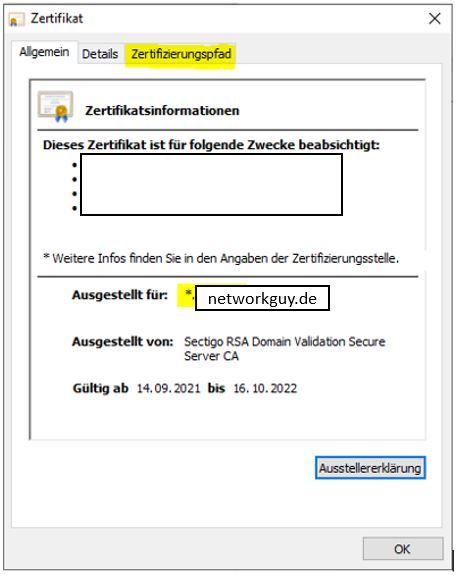
To do this, simply go to the Sophos SG webadmin or user portal with the Google Chrome browser and display the certificate.
Als erstens Exportierst du das Root CA.
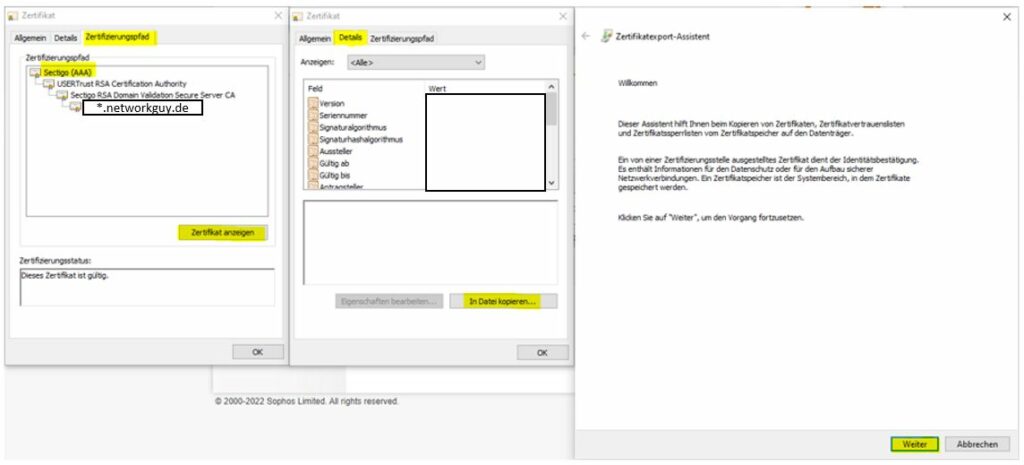
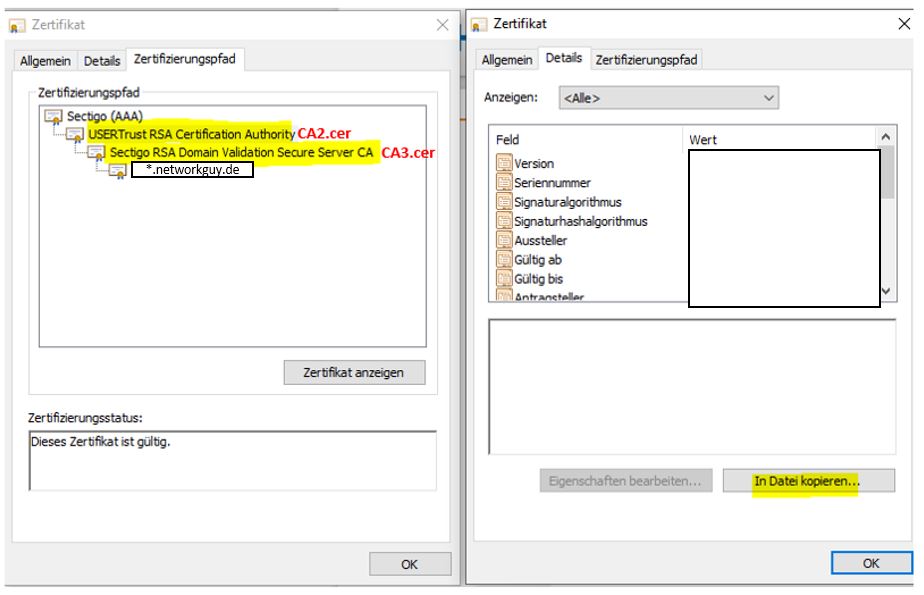
Click on the Root CA. Than details and Copy to files
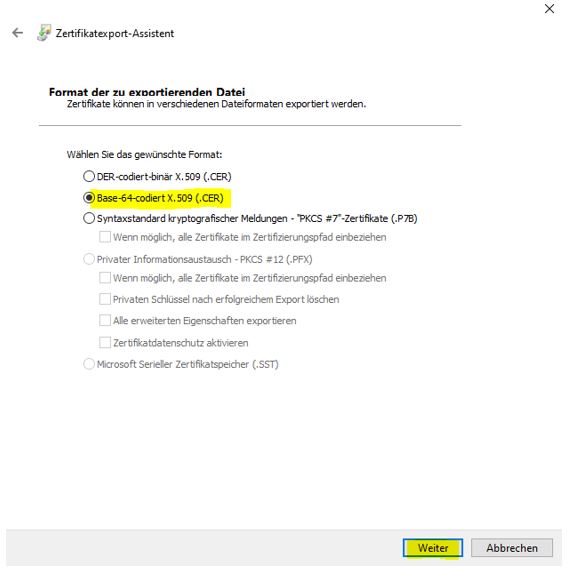
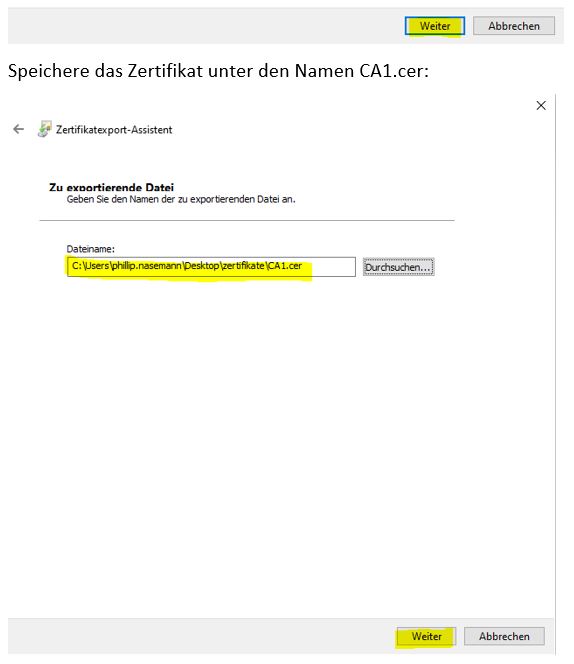
Save the certifiact as base 64
save it under the name CA1.cer
Repeat the steps for the two sub CAs.
build the certificate chain
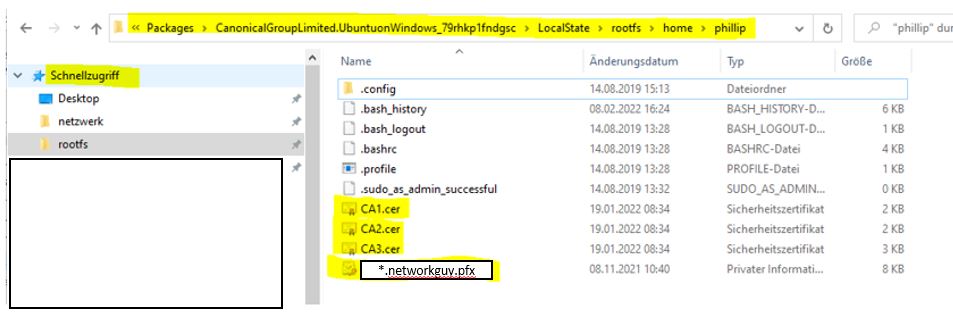
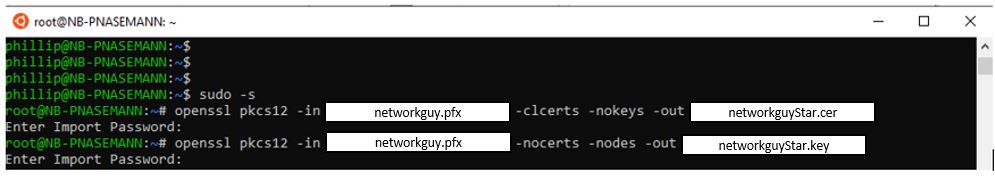
Now you have to detach the single certificate and the private key from the wildcard package without a certificate chain. The easiest way to do this is with openssl in a Linux machine. I have a Windows subsystem for Linux on my computer. Copy the wildcard certificate and the 3 certificates CA1 to CA3 into the home directory of the Linux machine.
For Ubuntu:
Detach the public and private keys from the certificate.
sudo -s openssl pkcs12 -in networkguy.pfx -clcerts -nokeys -out networkguyStar.cer openssl pkcs12 -in networkguy.pfx -nocerts -nodes -out networkguyStar.key
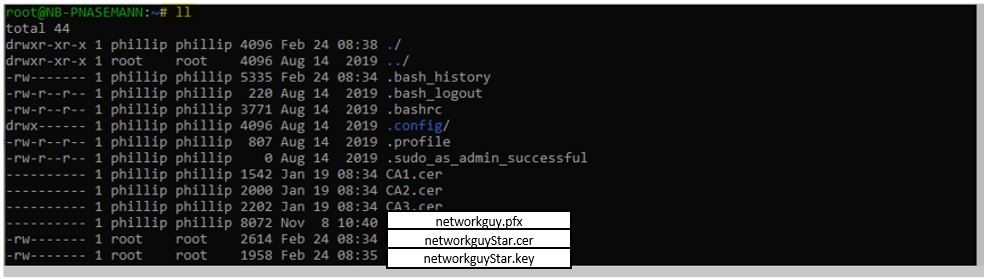
With ll you can now see that you now have the public key “networkguyStar.cer” and the private key “networkguyStar.key”.
Now we need to build a new wildcard certificate where the certificate chain has the order required by the Clearpass. The Clearpass wants the wildcard certificate first, then the sub CAs and finally the root CA.
The following command is required for this:
cat networkguyStar.cer CA3.cer CA2.cer CA1.cer > networkguyStarfullchain.cer
Now we have created a chain of certificates suitable for the Clearpass. :D
The Clearpass does not trust the Root or Sub CA
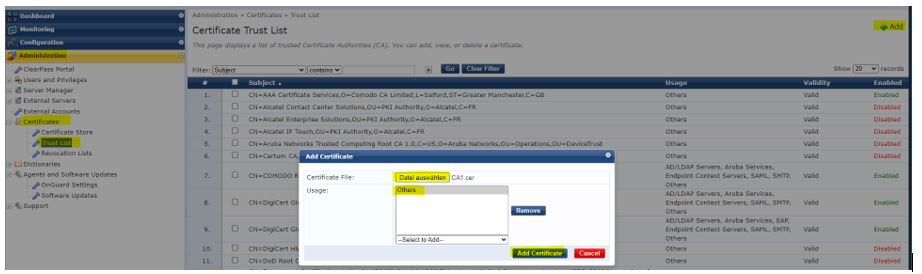
If the wildcard certificate contains a root or sub CA that Clearpass does not know, this must be imported. For this we can simply use the CA1.cer to CA3.cer.
To do this, go to Administration / Certificates / Trust List in the Policy Manager and then click on Add. Select Usage under -Select to Add– Other. Do this with CA1.cer, CA2.cer and CA3.cer.
Then have fun with your Clearpass. (A cool product) :D
Have a nice day!









6 Responses
Thanks, this did the trick for me also!
thank you, glad I could help.
Hi Phillip,
This was a great help…. Thank you . Keep it up.
thank you
Hi Philip, i have a MM/MD topology and i want to use CPPM for guest portla captive. Why should i use a wildcard certificate and i inject it into the controllers and CPPM ? have you onether solution for this ?
Hello Imed, with a wildcard certificate it is simply easiest, because you can use the wildcard certificate for the Clearpass and the MM/MD. You can also use any other trust certificate that contains the DNS name of your clearpass. If necessary, you can also use a self-signed certificate. But then the clients accessing the captive portal will get a certificate error.